Cybersecurity News
China-Linked APT31 Launches Stealthy Cyberattacks on Russian IT Using Cloud Services
The China-linked advanced persistent threat (APT) group known as APT31 has been attributed to cyber attacks targeting the Russian information technology (IT) sector between 2024 and 2025 while staying undetected for extended periods of time. "In the period from 2024 to 2025, the Russian IT sector, especially companies working as contractors and integrators of solutions for government agencies,
Read MoreMatrix Push C2 Uses Browser Notifications for Fileless, Cross-Platform Phishing Attacks
Bad actors are leveraging browser notifications as a vector for phishing attacks to distribute malicious links by means of a new command-and-control (C2) platform called Matrix Push C2. "This browser-native, fileless framework leverages push notifications, fake alerts, and link redirects to target victims across operating systems," Blackfog researcher Brenda Robb said in a Thursday report. In
Read MoreCISA Warns of Actively Exploited Critical Oracle Identity Manager Zero-Day Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a critical security flaw impacting Oracle Identity Manager to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability in question is CVE-2025-61757 (CVSS score: 9.8), a case of missing authentication for a critical function that can result in pre-authenticated
Read MoreGrafana Patches CVSS 10.0 SCIM Flaw Enabling Impersonation and Privilege Escalation
Grafana has released security updates to address a maximum severity security flaw that could allow privilege escalation or user impersonation under certain configurations. The vulnerability, tracked as CVE-2025-41115, carries a CVSS score of 10.0. It resides in the System for Cross-domain Identity Management (SCIM) component that allows automated user provisioning and management. First
Read MoreGoogle Brings AirDrop Compatibility to Android’s Quick Share Using Rust-Hardened Security
In a surprise move, Google on Thursday announced that it has updated Quick Share, its peer-to-peer file transfer service, to work with Apple's equipment AirDrop, allowing users to more easily share files and photos between Android and iPhone devices. The cross-platform sharing feature is currently limited to the Pixel 10 lineup and works with iPhone, iPad, and macOS devices, with plans to expand
Read MoreWhy IT Admins Choose Samsung for Mobile Security
Ever wonder how some IT teams keep corporate data safe without slowing down employees? Of course you have. Mobile devices are essential for modern work—but with mobility comes risk. IT admins, like you, juggle protecting sensitive data while keeping teams productive. That’s why more enterprises are turning to Samsung for mobile security. Hey—you're busy, so here's a quick-read article on what
Read MoreAPT24 Deploys BADAUDIO in Years-Long Espionage Hitting Taiwan and 1,000+ Domains
A China-nexus threat actor known as APT24 has been observed using a previously undocumented malware dubbed BADAUDIO to establish persistent remote access to compromised networks as part of a nearly three-year campaign. "While earlier operations relied on broad strategic web compromises to compromise legitimate websites, APT24 has recently pivoted to using more sophisticated vectors targeting
Read MoreSEC Drops SolarWinds Case After Years of High-Stakes Cybersecurity Scrutiny
The U.S. Securities and Exchange Commission (SEC) has abandoned its lawsuit against SolarWinds and its chief information security officer, alleging that the company had misled investors about the security practices that led to the 2020 supply chain attack. In a joint motion filed November 20, 2025, the SEC, along with SolarWinds and its CISO Timothy G. Brown, asked the court to voluntarily
Read MoreSalesforce Flags Unauthorized Data Access via Gainsight-Linked OAuth Activity
Salesforce has warned of detected "unusual activity" related to Gainsight-published applications connected to the platform. "Our investigation indicates this activity may have enabled unauthorized access to certain customers’ Salesforce data through the app's connection," the company said in an advisory. The cloud services firm said it has taken the step of revoking all active access and refresh
Read MoreShadowRay 2.0 Exploits Unpatched Ray Flaw to Build Self-Spreading GPU Cryptomining Botnet
Oligo Security has warned of ongoing attacks exploiting a two-year-old security flaw in the Ray open-source artificial intelligence (AI) framework to turn infected clusters with NVIDIA GPUs into a self-replicating cryptocurrency mining botnet. The activity, codenamed ShadowRay 2.0, is an evolution of a prior wave that was observed between September 2023 and March 2024. The attack, at its core,
Read MoreTsundere Botnet Expands Using Game Lures and Ethereum-Based C2 on Windows
Cybersecurity researchers have warned of an actively expanding botnet dubbed Tsundere that's targeting Windows users. Active since mid-2025, the threat is designed to execute arbitrary JavaScript code retrieved from a command-and-control (C2) server, Kaspersky researcher Lisandro Ubiedo said in an analysis published today. There are currently no details on how the botnet malware is propagated;
Read MoreThreatsDay Bulletin: 0-Days, LinkedIn Spies, Crypto Crimes, IoT Flaws and New Malware Waves
This week has been crazy in the world of hacking and online security. From Thailand to London to the US, we've seen arrests, spies at work, and big power moves online. Hackers are getting caught. Spies are getting better at their jobs. Even simple things like browser add-ons and smart home gadgets are being used to attack people. Every day, there's a new story that shows how quickly things are
Read MoreCTM360 Exposes a Global WhatsApp Hijacking Campaign: HackOnChat
CTM360 has identified a rapidly expanding WhatsApp account-hacking campaign targeting users worldwide via a network of deceptive authentication portals and impersonation pages. The campaign, internally dubbed HackOnChat, abuses WhatsApp’s familiar web interface, using social engineering tactics to trick users into compromising their accounts. Investigators identified thousands of malicious URLs
Read MoreNew Sturnus Android Trojan Quietly Captures Encrypted Chats and Hijacks Devices
Cybersecurity researchers have disclosed details of a new Android banking trojan called Sturnus that enables credential theft and full device takeover to conduct financial fraud. "A key differentiator is its ability to bypass encrypted messaging," ThreatFabric said in a report shared with The Hacker News. "By capturing content directly from the device screen after decryption, Sturnus can monitor
Read MoreIran-Linked Hackers Mapped Ship AIS Data Days Before Real-World Missile Strike Attempt
Threat actors with ties to Iran engaged in cyber warfare as part of efforts to facilitate and enhance physical, real-world attacks, a trend that Amazon has called cyber-enabled kinetic targeting. The development is a sign that the lines between state-sponsored cyber attacks and kinetic warfare are increasingly blurring, necessitating the need for a new category of warfare, the tech giant's
Read MoreTamperedChef Malware Spreads via Fake Software Installers in Ongoing Global Campaign
Threat actors are leveraging bogus installers masquerading as popular software to trick users into installing malware as part of a global malvertising campaign dubbed TamperedChef. The end goal of the attacks is to establish persistence and deliver JavaScript malware that facilitates remote access and control, per a new report from Acronis Threat Research Unit (TRU). The campaign, per the
Read MoreNHS Warns of PoC Exploit for 7-Zip Symbolic Link–Based RCE Vulnerability
Update: The NHS England Digital, in an updated advisory on November 20, 2025, said it has not observed in-the-wild exploitation of CVE-2025-11001, but noted that it's "aware of a public proof-of-concept exploit." It has since removed what it said were "erroneous references" to active exploitation.The original story follows below - A recently disclosed security flaw impacting 7-Zip has come
Read MorePython-Based WhatsApp Worm Spreads Eternidade Stealer Across Brazilian Devices
Cybersecurity researchers have disclosed details of a new campaign that leverages a combination of social engineering and WhatsApp hijacking to distribute a Delphi-based banking trojan named Eternidade Stealer as part of attacks targeting users in Brazil. "It uses Internet Message Access Protocol (IMAP) to dynamically retrieve command-and-control (C2) addresses, allowing the threat actor to
Read MoreWrtHug Exploits Six ASUS WRT Flaws to Hijack Tens of Thousands of EoL Routers Worldwide
A newly discovered campaign has compromised tens of thousands of outdated or end-of-life (EoL) ASUS routers worldwide, predominantly in Taiwan, the U.S., and Russia, to rope them into a massive network. The router hijacking activity has been codenamed Operation WrtHug by SecurityScorecard's STRIKE team. Southeast Asia and European countries are some of the other regions where infections have
Read MoreApplication Containment: How to Use Ringfencing to Prevent the Weaponization of Trusted Software
The challenge facing security leaders is monumental: Securing environments where failure is not an option. Reliance on traditional security postures, such as Endpoint Detection and Response (EDR) to chase threats after they have already entered the network, is fundamentally risky and contributes significantly to the half-trillion-dollar annual cost of cybercrime. Zero Trust fundamentally shifts
Read MoreEdgeStepper Implant Reroutes DNS Queries to Deploy Malware via Hijacked Software Updates
The threat actor known as PlushDaemon has been observed using a previously undocumented Go-based network backdoor codenamed EdgeStepper to facilitate adversary-in-the-middle (AitM) attacks. EdgeStepper "redirects all DNS queries to an external, malicious hijacking node, effectively rerouting the traffic from legitimate infrastructure used for software updates to attacker-controlled infrastructure
Read MoreServiceNow AI Agents Can Be Tricked Into Acting Against Each Other via Second-Order Prompts
Malicious actors can exploit default configurations in ServiceNow's Now Assist generative artificial intelligence (AI) platform and leverage its agentic capabilities to conduct prompt injection attacks. The second-order prompt injection, according to AppOmni, makes use of Now Assist's agent-to-agent discovery to execute unauthorized actions, enabling attackers to copy and exfiltrate sensitive
Read MoreFortinet Warns of New FortiWeb CVE-2025-58034 Vulnerability Exploited in the Wild
Fortinet has warned of a new security flaw in FortiWeb that it said has been exploited in the wild. The medium-severity vulnerability, tracked as CVE-2025-58034, carries a CVSS score of 6.7 out of a maximum of 10.0. "An Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') vulnerability [CWE-78] in FortiWeb may allow an authenticated attacker to execute
Read MoreSneaky 2FA Phishing Kit Adds BitB Pop-ups Designed to Mimic the Browser Address Bar
The malware authors associated with a Phishing-as-a-Service (PhaaS) kit known as Sneaky 2FA have incorporated Browser-in-the-Browser (BitB) functionality into their arsenal, underscoring the continued evolution of such offerings and further making it easier for less-skilled threat actors to mount attacks at scale. Push Security, in a report shared with The Hacker News, said it observed the use
Read MoreMeta Expands WhatsApp Security Research with New Proxy Tool and $4M in Bounties This Year
Meta on Tuesday said it has made available a tool called WhatsApp Research Proxy to some of its long-time bug bounty researchers to help improve the program and more effectively research the messaging platform's network protocol. The idea is to make it easier to delve into WhatsApp-specific technologies as the application continues to be a lucrative attack surface for state-sponsored actors and
Read MoreLearn How Leading Companies Secure Cloud Workloads and Infrastructure at Scale
You’ve probably already moved some of your business to the cloud—or you’re planning to. That’s a smart move. It helps you work faster, serve your customers better, and stay ahead. But as your cloud setup grows, it gets harder to control who can access what. Even one small mistake—like the wrong person getting access—can lead to big problems. We're talking data leaks, legal trouble, and serious
Read MoreResearchers Detail Tuoni C2's Role in an Attempted 2025 Real-Estate Cyber Intrusion
Cybersecurity researchers have disclosed details of a cyber attack targeting a major U.S.-based real-estate company that involved the use of a nascent command-and-control (C2) and red teaming framework known as Tuoni. "The campaign leveraged the emerging Tuoni C2 framework, a relatively new, command-and-control (C2) tool (with a free license) that delivers stealthy, in-memory payloads,"
Read MoreIranian Hackers Use DEEPROOT and TWOSTROKE Malware in Aerospace and Defense Attacks
Suspected espionage-driven threat actors from Iran have been observed deploying backdoors like TWOSTROKE and DEEPROOT as part of continued attacks aimed at aerospace, aviation, and defense industries in the Middle East. The activity has been attributed by Google-owned Mandiant to a threat cluster tracked as UNC1549 (aka GalaxyGato, Nimbus Manticore, or Subtle Snail), which was first documented
Read MoreBeyond IAM Silos: Why the Identity Security Fabric is Essential for Securing AI and Non-Human Identities
Identity security fabric (ISF) is a unified architectural framework that brings together disparate identity capabilities. Through ISF, identity governance and administration (IGA), access management (AM), privileged access management (PAM), and identity threat detection and response (ITDR) are all integrated into a single, cohesive control plane. Building on Gartner’s definition of “identity
Read MoreSeven npm Packages Use Adspect Cloaking to Trick Victims Into Crypto Scam Pages
Cybersecurity researchers have discovered a set of seven npm packages published by a single threat actor that leverages a cloaking service called Adspect to differentiate between real victims and security researchers to ultimately redirect them to sketchy crypto-themed sites. The malicious npm packages, published by a threat actor named "dino_reborn" between September and November 2025, are
Read MoreMicrosoft Mitigates Record 15.72 Tbps DDoS Attack Driven by AISURU Botnet
Microsoft on Monday disclosed that it automatically detected and neutralized a distributed denial-of-service (DDoS) attack targeting a single endpoint in Australia that measured 15.72 terabits per second (Tbps) and nearly 3.64 billion packets per second (pps). The tech giant said it was the largest DDoS attack ever observed in the cloud, and that it originated from a TurboMirai-class Internet of
Read MoreGoogle Issues Security Fix for Actively Exploited Chrome V8 Zero-Day Vulnerability
Google on Monday released security updates for its Chrome browser to address two security flaws, including one that has come under active exploitation in the wild. The vulnerability in question is CVE-2025-13223 (CVSS score: 8.8), a type confusion vulnerability in the V8 JavaScript and WebAssembly engine that could be exploited to achieve arbitrary code execution or program crashes. "Type
Read MoreNew EVALUSION ClickFix Campaign Delivers Amatera Stealer and NetSupport RAT
Cybersecurity researchers have discovered malware campaigns using the now-prevalent ClickFix social engineering tactic to deploy Amatera Stealer and NetSupport RAT. The activity, observed this month, is being tracked by eSentire under the moniker EVALUSION. First spotted in June 2025, Amatera is assessed to be an evolution of ACR (short for "AcridRain") Stealer, which was available under the
Read More⚡ Weekly Recap: Fortinet Exploited, China's AI Hacks, PhaaS Empire Falls & More
This week showed just how fast things can go wrong when no one’s watching. Some attacks were silent and sneaky. Others used tools we trust every day — like AI, VPNs, or app stores — to cause damage without setting off alarms. It’s not just about hacking anymore. Criminals are building systems to make money, spy, or spread malware like it’s a business. And in some cases, they’re using the same
Read More5 Reasons Why Attackers Are Phishing Over LinkedIn
Phishing attacks are no longer confined to the email inbox, with 1 in 3 phishing attacks now taking place over non-email channels like social media, search engines, and messaging apps. LinkedIn in particular has become a hotbed for phishing attacks, and for good reason. Attackers are running sophisticated spear-phishing attacks against company executives, with recent campaigns seen targeting
Read MoreDragon Breath Uses RONINGLOADER to Disable Security Tools and Deploy Gh0st RAT
The threat actor known as Dragon Breath has been observed making use of a multi-stage loader codenamed RONINGLOADER to deliver a modified variant of a remote access trojan called Gh0st RAT. The campaign, which is primarily aimed at Chinese-speaking users, employs trojanized NSIS installers masquerading as legitimate like Google Chrome and Microsoft Teams, according to Elastic Security Labs. "The
Read MoreRust Adoption Drives Android Memory Safety Bugs Below 20% for First Time
Google has disclosed that the company's continued adoption of the Rust programming language in Android has resulted in the number of memory safety vulnerabilities falling below 20% of total vulnerabilities for the first time. "We adopted Rust for its security and are seeing a 1000x reduction in memory safety vulnerability density compared to Android’s C and C++ code. But the biggest surprise was
Read MoreRondoDox Exploits Unpatched XWiki Servers to Pull More Devices Into Its Botnet
The botnet malware known as RondoDox has been observed targeting unpatched XWiki instances against a critical security flaw that could allow attackers to achieve arbitrary code execution. The vulnerability in question is CVE-2025-24893 (CVSS score: 9.8), an eval injection bug that could allow any guest user to perform arbitrary remote code execution through a request to the "/bin/get/Main/
Read MoreFive Plead Guilty in U.S. for Helping North Korean IT Workers Infiltrate 136 Companies
The U.S. Department of Justice (DoJ) on Friday announced that five individuals have pleaded guilty to assisting North Korea's illicit revenue generation schemes by enabling information technology (IT) worker fraud in violation of international sanctions. The five individuals are listed below - Audricus Phagnasay, 24 Jason Salazar, 30 Alexander Paul Travis, 34 Oleksandr Didenko, 28, and Erick
Read MoreNorth Korean Hackers Turn JSON Services into Covert Malware Delivery Channels
The North Korean threat actors behind the Contagious Interview campaign have once again tweaked their tactics by using JSON storage services to stage malicious payloads. "The threat actors have recently resorted to utilizing JSON storage services like JSON Keeper, JSONsilo, and npoint.io to host and deliver malware from trojanized code projects, with the lure," NVISO researchers Bart Parys, Stef
Read MoreResearchers Find Serious AI Bugs Exposing Meta, Nvidia, and Microsoft Inference Frameworks
Cybersecurity researchers have uncovered critical remote code execution vulnerabilities impacting major artificial intelligence (AI) inference engines, including those from Meta, Nvidia, Microsoft, and open-source PyTorch projects such as vLLM and SGLang. "These vulnerabilities all traced back to the same root cause: the overlooked unsafe use of ZeroMQ (ZMQ) and Python's pickle deserialization,"
Read MoreIranian Hackers Launch ‘SpearSpecter’ Spy Operation on Defense & Government Targets
The Iranian state-sponsored threat actor known as APT42 has been observed targeting individuals and organizations that are of interest to the Islamic Revolutionary Guard Corps (IRGC) as part of a new espionage-focused campaign. The activity, detected in early September 2025 and assessed to be ongoing, has been codenamed SpearSpecter by the Israel National Digital Agency (INDA). "The
Read MoreRansomware's Fragmentation Reaches a Breaking Point While LockBit Returns
Key Takeaways: 85 active ransomware and extortion groups observed in Q3 2025, reflecting the most decentralized ransomware ecosystem to date. 1,590 victims disclosed across 85 leak sites, showing high, sustained activity despite law-enforcement pressure. 14 new ransomware brands launched this quarter, proving how quickly affiliates reconstitute after takedowns. LockBit’s reappearance with
Read MoreChinese Hackers Use Anthropic's AI to Launch Automated Cyber Espionage Campaign
State-sponsored threat actors from China used artificial intelligence (AI) technology developed by Anthropic to orchestrate automated cyber attacks as part of a "highly sophisticated espionage campaign" in mid-September 2025. "The attackers used AI's 'agentic' capabilities to an unprecedented degree – using AI not just as an advisor, but to execute the cyber attacks themselves," the AI upstart
Read MoreNow-Patched Fortinet FortiWeb Flaw Exploited in Attacks to Create Admin Accounts
Cybersecurity researchers are sounding the alert about an authentication bypass vulnerability in Fortinet FortiWeb Web Application Firewall (WAF) that could allow an attacker to take over admin accounts and completely compromise a device. "The watchTowr team is seeing active, indiscriminate in-the-wild exploitation of what appears to be a silently patched vulnerability in Fortinet's FortiWeb
Read MoreRussian Hackers Create 4,300 Fake Travel Sites to Steal Hotel Guests' Payment Data
A Russian-speaking threat behind an ongoing, mass phishing campaign has registered more than 4,300 domain names since the start of the year. The activity, per Netcraft security researcher Andrew Brandt, is designed to target customers of the hospitality industry, specifically hotel guests who may have travel reservations with spam emails. The campaign is said to have begun in earnest around
Read MoreFake Chrome Extension “Safery” Steals Ethereum Wallet Seed Phrases Using Sui Blockchain
Cybersecurity researchers have uncovered a malicious Chrome extension that poses as a legitimate Ethereum wallet but harbors functionality to exfiltrate users' seed phrases. The name of the extension is "Safery: Ethereum Wallet," with the threat actor describing it as a "secure wallet for managing Ethereum cryptocurrency with flexible settings." It was uploaded to the Chrome Web Store on
Read MoreWhen Attacks Come Faster Than Patches: Why 2026 Will be the Year of Machine-Speed Security
The Race for Every New CVE Based on multiple 2025 industry reports: roughly 50 to 61 percent of newly disclosed vulnerabilities saw exploit code weaponized within 48 hours. Using the CISA Known Exploited Vulnerabilities Catalog as a reference, hundreds of software flaws are now confirmed as actively targeted within days of public disclosure. Each new announcement now triggers a global race
Read MoreOperation Endgame Dismantles Rhadamanthys, Venom RAT, and Elysium Botnet in Global Crackdown
Malware families like Rhadamanthys Stealer, Venom RAT, and the Elysium botnet have been disrupted as part of a coordinated law enforcement operation led by Europol and Eurojust. The activity, which took place between November 10 and 13, 2025, marks Please remove image compression the latest phase of Operation Endgame, an ongoing operation designed to take down criminal infrastructures and combat
Read MoreThreatsDay Bulletin: Cisco 0-Days, AI Bug Bounties, Crypto Heists, State-Linked Leaks and 20 More Stories
Behind every click, there’s a risk waiting to be tested. A simple ad, email, or link can now hide something dangerous. Hackers are getting smarter, using new tools to sneak past filters and turn trusted systems against us. But security teams are fighting back. They’re building faster defenses, better ways to spot attacks, and stronger systems to keep people safe. It’s a constant race — every
Read MoreMozilla Says It’s Finally Done With Two-Faced Onerep
In March 2024, Mozilla said it was winding down its collaboration with Onerep -- an identity protection service offered with the Firefox web browser that promises to remove users from hundreds of people-search sites -- after KrebsOnSecurity revealed Onerep's founder had created dozens of people-search services and was continuing to operate at least one of them. Sixteen months later, however, Mozilla is still promoting Onerep. This week, Mozilla announced their partnership with Onerep will officially end next month.
Read MoreThe Cloudflare Outage May Be a Security Roadmap
An intermittent outage at Cloudflare on Tuesday briefly knocked many of the Internet's top destinations offline. Some affected Cloudflare customers were able to pivot away from the platform temporarily so that visitors could still access their websites. But security experts say doing so may have also triggered an impromptu network penetration test for organizations that have come to rely on Cloudflare to block many types of abusive and malicious traffic.
Read MoreMicrosoft Patch Tuesday, November 2025 Edition
Microsoft this week pushed security updates to fix more than 60 vulnerabilities in its Windows operating systems and supported software, including at least one zero-day bug that is already being exploited. Microsoft also fixed a glitch that prevented some Windows 10 users from taking advantage of an extra year of security updates, which is nice because the zero-day flaw and other critical weaknesses patched today affect all versions of Windows, including Windows 10.
Read MoreGoogle Sues to Disrupt Chinese SMS Phishing Triad
Google is suing more than two dozen unnamed individuals allegedly involved in peddling a popular China-based mobile phishing service that helps scammers impersonate hundreds of trusted brands, blast out text message lures, and convert phished payment card data into mobile wallets from Apple and Google.
Read MoreDrilling Down on Uncle Sam’s Proposed TP-Link Ban
The U.S. government is reportedly preparing to ban the sale of wireless routers and other networking gear from TP-Link Systems, a tech company that currently enjoys an estimated 50% market share among home users and small businesses. Experts say while the proposed ban may have more to do with TP-Link's ties to China than any specific technical threats, much of the rest of the industry serving this market also sources hardware from China and ships products that are insecure fresh out of the box.
Read MoreCloudflare Scrubs Aisuru Botnet from Top Domains List
For the past week, domains associated with the massive Aisuru botnet have repeatedly usurped Amazon, Apple, Google and Microsoft in Cloudflare's public ranking of the most frequently requested websites. Cloudflare responded by redacting Aisuru domain names from their top websites list. The chief executive at Cloudflare says Aisuru's overlords are using the botnet to boost their malicious domain rankings, while simultaneously attacking the company's domain name system (DNS) service.
Read MoreAlleged Jabber Zeus Coder ‘MrICQ’ in U.S. Custody
A Ukrainian man indicted in 2012 for conspiring with a prolific hacking group to steal tens of millions of dollars from U.S. businesses was arrested in Italy and is now in custody in the United States, KrebsOnSecurity has learned. Sources close to the investigation say Yuriy Igorevich Rybtsov, a 41-year-old from the Russia-controlled city of Donetsk, Ukraine, was previously referenced in U.S. federal charging documents only by his online handle "MrICQ." According to a 13-year-old indictment filed by prosecutors in Nebraska, MrICQ was a developer for a cybercrime group known as "Jabber Zeus."
Read MoreAisuru Botnet Shifts from DDoS to Residential Proxies
Aisuru, the botnet responsible for a series of record-smashing distributed denial-of-service (DDoS) attacks this year, recently was overhauled to support a more low-key, lucrative and sustainable business: Renting hundreds of thousands of infected Internet of Things (IoT) devices to proxy services that help cybercriminals anonymize their traffic. Experts says a glut of proxies from Aisuru and other sources is fueling large-scale data harvesting efforts tied to various artificial intelligence (AI) projects, helping content scrapers evade detection by routing their traffic through residential connections that appear to be regular Internet users.
Read MoreCanada Fines Cybercrime Friendly Cryptomus $176M
Financial regulators in Canada this week levied $176 million in fines against Cryptomus, a digital payments platform that supports dozens of Russian cryptocurrency exchanges and websites hawking cybercrime services. The penalties for violating Canada's anti money-laundering laws come ten months after KrebsOnSecurity noted that Cryptomus's Vancouver street address was home to dozens of foreign currency dealers, money transfer businesses, and cryptocurrency exchanges — none of which were physically located there.
Read MoreEmail Bombs Exploit Lax Authentication in Zendesk
Cybercriminals are abusing a widespread lack of authentication in the customer service platform Zendesk to flood targeted email inboxes with menacing messages that come from hundreds of Zendesk corporate customers simultaneously.
Read MoreMore on Rewiring Democracy
It’s been a month since Rewiring Democracy: How AI Will Transform Our Politics, Government, and Citizenship was published. From what we know, sales are good.
Some of the book’s forty-three chapters are available online: chapters 2, 12, 28, 34, 38, and 41.
We need more reviews—six on Amazon is not enough, and no one has yet posted a viral TikTok review. One review was published in Nature and another on the RSA Conference website, but more would be better. If you’ve read the book, please leave a review somewhere.
My coauthor and I have been doing all sort of book events, both online and in person. This ...
Read MoreAI as Cyberattacker
From Anthropic:
Read MoreIn mid-September 2025, we detected suspicious activity that later investigation determined to be a highly sophisticated espionage campaign. The attackers used AI’s “agentic” capabilities to an unprecedented degree—using AI not just as an advisor, but to execute the cyberattacks themselves.
The threat actor—whom we assess with high confidence was a Chinese state-sponsored group—manipulated our Claude Code tool into attempting infiltration into roughly thirty global targets and succeeded in a small number of cases. The operation targeted large tech companies, financial institutions, chemical manufacturing companies, and government agencies. We believe this is the first documented case of a large-scale cyberattack executed without substantial human intervention...
Scam USPS and E-Z Pass Texts and Websites
Google has filed a complaint in court that details the scam:
Read MoreIn a complaint filed Wednesday, the tech giant accused “a cybercriminal group in China” of selling “phishing for dummies” kits. The kits help unsavvy fraudsters easily “execute a large-scale phishing campaign,” tricking hordes of unsuspecting people into “disclosing sensitive information like passwords, credit card numbers, or banking information, often by impersonating well-known brands, government agencies, or even people the victim knows.”
These branded “Lighthouse” kits offer two versions of software, depending on whether bad actors want to launch SMS and e-commerce scams. “Members may subscribe to weekly, monthly, seasonal, annual, or permanent licenses,” Google alleged. Kits include “hundreds of templates for fake websites, domain set-up tools for those fake websites, and other features designed to dupe victims into believing they are entering sensitive information on a legitimate website.”...
Legal Restrictions on Vulnerability Disclosure
Kendra Albert gave an excellent talk at USENIX Security this year, pointing out that the legal agreements surrounding vulnerability disclosure muzzle researchers while allowing companies to not fix the vulnerabilities—exactly the opposite of what the responsible disclosure movement of the early 2000s was supposed to prevent. This is the talk.
Read MoreThirty years ago, a debate raged over whether vulnerability disclosure was good for computer security. On one side, full disclosure advocates argued that software bugs weren’t getting fixed and wouldn’t get fixed if companies that made insecure software wasn’t called out publicly. On the other side, companies argued that full disclosure led to exploitation of unpatched vulnerabilities, especially if they were hard to fix. After blog posts, public debates, and countless mailing list flame wars, there emerged a compromise solution: coordinated vulnerability disclosure, where vulnerabilities were disclosed after a period of confidentiality where vendors can attempt to fix things. Although full disclosure fell out of fashion, disclosure won and security through obscurity lost. We’ve lived happily ever after since...
AI and Voter Engagement
Social media has been a familiar, even mundane, part of life for nearly two decades. It can be easy to forget it was not always that way.
In 2008, social media was just emerging into the mainstream. Facebook reached 100 million users that summer. And a singular candidate was integrating social media into his political campaign: Barack Obama. His campaign’s use of social media was so bracingly innovative, so impactful, that it was viewed by journalist David Talbot and others as the strategy that enabled the first term Senator to win the White House...
Read MoreMore Prompt||GTFO
The next three in this series on online events highlighting interesting uses of AI in cybersecurity are online: #4, #5, and #6. Well worth watching.
Read MoreFriday Squid Blogging: Pilot Whales Eat a Lot of Squid
Short-finned pilot wales (Globicephala macrorhynchus) eat at lot of squid:
Read MoreTo figure out a short-finned pilot whale’s caloric intake, Gough says, the team had to combine data from a variety of sources, including movement data from short-lasting tags, daily feeding rates from satellite tags, body measurements collected via aerial drones, and sifting through the stomachs of unfortunate whales that ended up stranded on land.
Once the team pulled all this data together, they estimated that a typical whale will eat between 82 and 202 squid a day. To meet their energy needs, a whale will have to consume an average of 140 squid a day. Annually, that’s about 74,000 squid per whale. For all the whales in the area, that amounts to about 88,000 tons of squid eaten every year...
Upcoming Speaking Engagements
This is a current list of where and when I am scheduled to speak:
- My coauthor Nathan E. Sanders and I are speaking at the Rayburn House Office Building in Washington, DC at noon ET on November 17, 2025. The event is hosted by the POPVOX Foundation and the topic is “AI and Congress: Practical Steps to Govern and Prepare.”
- I’m speaking on “Integrity and Trustworthy AI” at North Hennepin Community College in Brooklyn Park, Minnesota, USA, on Friday, November 21, 2025, at 2:00 PM CT. The event is cohosted by the college and The Twin Cities IEEE Computer Society...
The Role of Humans in an AI-Powered World
As AI capabilities grow, we must delineate the roles that should remain exclusively human. The line seems to be between fact-based decisions and judgment-based decisions.
For example, in a medical context, if an AI was demonstrably better at reading a test result and diagnosing cancer than a human, you would take the AI in a second. You want the more accurate tool. But justice is harder because justice is inherently a human quality in a way that “Is this tumor cancerous?” is not. That’s a fact-based question. “What’s the right thing to do here?” is a human-based question...
Read MoreBlack Friday TV deals are live now with massive sales: Here are our 40+ top picks
Black Friday is less than a week away, and I'm already tracking great deals on TVs and home theater equipment from Samsung, Sony, and more live.
Read MoreRoku vs. Fire Stick: I compared the best streaming devices in 2025, and here's the winner
Two of the top streaming devices in 2025 are on sale before Black Friday. Here's how to decide which deal is best for you.
Read MoreThese 12+ oddball tools are surprisingly useful, and they're all on sale right now
Black Friday is a few days away, but I've been searching the web looking for the most useful gadgets that make great gifts.
Read MoreThousands of readers bought this smartwatch this year (it's not from Apple, Samsung, or Google)
We found the top 10 smartwatches and fitness trackers our readers bought most this year, and there were several surprises on the list.
Read MoreThe base model Kindle is the e-reader most people should buy, and it's only $80 right now
The base model Kindle is ideal for most users, and it's available for under $100 during Amazon's Black Friday sale.
Read MoreBest Walmart Black Friday deals live now: Save up to 60% on AirPods, TVs, Dyson vacuums, and more
Walmart's early Black Friday deals are here, with big discounts on laptops, kitchen gadgets, and more (including the lowest-ever prices on AirTags, AirPods, and Apple Watches).
Read MoreMy favorite smart bulbs add ambience to any home, and they're under $20 for Black Friday
The GE Cync smart bulbs let you control the lighting and mood of your home. Currently, a two-pack is 25% off, ahead of Black Friday.
Read MoreAmazon's 2025 Black Friday deals are shockingly good: Shop some of my favorites up to 60% off
Black Friday is less than a week away, but Amazon's Black Friday deals are already here. These are my favorite deals so far, like the Oura Ring 4 for 30% off.
Read MoreThis wall-mounted smart calendar can get you organized before the new year (and it's on sale)
In my ongoing effort to stay organized, the 15-inch Skylight Calendar smart display has made the biggest difference. It's 22% off for Black Friday.
Read MoreThese sleep earbuds can dim out distracting noise, and they're not made by Bose or Anker
Ozlo's Sleepbuds are on sale for $75 off during Black Friday sales -- the lowest price we've ever seen.
Read MoreBest early Black Friday PlayStation deals 2025: 20 sales out now
Black Friday is less than a week away, but you can already find great PlayStation deals now from Amazon, Target, Walmart, and others. I've collected some of the best.
Read MoreI found the best early Black Friday streaming service and device deals
Black Friday is days away, but we've already found great streaming deals, including over 50% off Apple TV.
Read MoreBest early Black Friday laptop deals 2025: 20+ sales live now
Black Friday is less than a week away, but the big sales are kicking off now. Here are the best laptop deals we've found so far, including the new MacBook Air M4 for 25% off.
Read More10 most popular phones this year, according to thousands of readers (and no.1 is bananas)
Here are the most popular phones purchased by our readers this year, including familiar picks and a major upset.
Read MoreOwn AirPods? I changed these 3 iPhone settings for an instant audio boost
If you rushed through your AirPods setup, revisit these features to get the best performance.
Read MoreThis Apple Watch model is still my favorite - and it's the cheapest one you can buy new
I still love the Apple Watch SE 2 for its useful features and fair price, especially when it's on sale for Black Friday.
Read MoreSeriously, Verizon is giving away free Samsung 4K TVs for Black Friday - how to qualify
If you ever needed a reason to upgrade your home internet plan, let this be one to consider.
Read MoreThis do-it-all cable is a must-have travel item (and it's under $15 right now)
The Statik PowerPivot Pro features a 180-degree swivel mechanism and a pull-out Type-A port, making it a 2-in-1 wire.
Read MoreThe GE Opal nugget ice maker makes the good ice, and it's $160 off for Black Friday
Whether you call it the good ice, Sonic ice, or soft ice, you can now have it from the comfort of your kitchen.
Read MoreBest early Black Friday Verizon deals 2025: How to qualify for a free iPhone, Samsung, or Pixel
If you're a Big Red customer (or soon to be), these early Black Friday offers will net you a new phone, tablet, gaming console, and more for less than retail.
Read MoreIn Other News: ATM Jackpotting, WhatsApp-NSO Lawsuit Continues, CISA Hiring
Other noteworthy stories that might have slipped under the radar: surge in Palo Alto Networks scanning, WEL Companies data breach impacts 120,000 people, AI second-order prompt injection attack.
The post In Other News: ATM Jackpotting, WhatsApp-NSO Lawsuit Continues, CISA Hiring appeared first on SecurityWeek.
Read MoreCritical Oracle Identity Manager Flaw Possibly Exploited as Zero-Day
CVE-2025-61757 is an unauthenticated remote code execution vulnerability affecting Oracle Identity Manager.
The post Critical Oracle Identity Manager Flaw Possibly Exploited as Zero-Day appeared first on SecurityWeek.
Read MoreOver 370 Organizations Take Part in GridEx VIII Grid Security Exercise
The number of participants in the cyber and physical grid security exercise increased by nearly 50% compared to two years ago.
The post Over 370 Organizations Take Part in GridEx VIII Grid Security Exercise appeared first on SecurityWeek.
Read MoreSonicWall Patches High-Severity Flaws in Firewalls, Email Security Appliance
The vulnerabilities could be exploited to cause a denial-of-service (DoS) condition, execute arbitrary code, or access arbitrary files and directories.
The post SonicWall Patches High-Severity Flaws in Firewalls, Email Security Appliance appeared first on SecurityWeek.
Read MoreChinese Cyberspies Deploy ‘BadAudio’ Malware via Supply Chain Attacks
APT24 has been relying on various techniques to drop the BadAudio downloader and then deploy additional payloads.
The post Chinese Cyberspies Deploy ‘BadAudio’ Malware via Supply Chain Attacks appeared first on SecurityWeek.
Read MoreSquareX and Perplexity Quarrel Over Alleged Comet Browser Vulnerability
SquareX claims to have found a way to abuse a hidden Comet API to execute local commands, but Perplexity says the research is fake.
The post SquareX and Perplexity Quarrel Over Alleged Comet Browser Vulnerability appeared first on SecurityWeek.
Read MoreRunlayer Emerges From Stealth Mode With $11 Million in Funding
The company has operated in stealth mode for four months and has signed dozens of customers, including eight unicorns.
The post Runlayer Emerges From Stealth Mode With $11 Million in Funding appeared first on SecurityWeek.
Read MoreSalesforce Instances Hacked via Gainsight Integrations
The infamous ShinyHunters hackers have targeted customer-managed Gainsight-published applications to steal data from Salesforce instances.
The post Salesforce Instances Hacked via Gainsight Integrations appeared first on SecurityWeek.
Read MoreRussian Hacking Suspect Wanted by the FBI Arrested on Thai Resort Island
Thailand’s Cyber Crime Investigation Bureau said an FBI tip that the “world-class hacker” was traveling to Thailand led to his arrest in Phuket.
The post Russian Hacking Suspect Wanted by the FBI Arrested on Thai Resort Island appeared first on SecurityWeek.
Read MoreNew Sturnus Banking Trojan Targets WhatsApp, Telegram, Signal Messages
The Android malware is in development and appears to be mainly aimed at users in Europe.
The post New Sturnus Banking Trojan Targets WhatsApp, Telegram, Signal Messages appeared first on SecurityWeek.
Read MoreShinyHunters 'does not like Salesforce at all,' claims the crew accessed Gainsight 3 months ago
Shiny talks to The Reg
EXCLUSIVE ShinyHunters has claimed responsibility for the Gainsight breach that allowed the data thieves to snarf data from hundreds more Salesforce customers.…
Read MoreFour charged over alleged plot to smuggle Nvidia AI chips into China
Prosecutors say front companies, falsified paperwork, and overseas drop points used to dodge US export rules
Four people have been charged in the US with plotting to funnel restricted Nvidia AI chips into China, allegedly relying on shell firms, fake invoices, and covert routing to slip cutting-edge GPUs past American export controls.…
Read MoreRussia-linked crooks bought a bank for Christmas to launder cyber loot
UK cops trace street-level crime to sanctions-busting networks tied to Moscow's war economy
On Christmas Day 2024, a Russian-linked laundering network bought itself a very special present: a controlling stake in a Kyrgyzstan bank, later used to wash cybercrime profits and funnel money into Moscow's war machine, according to the UK's National Crime Agency (NCA).…
Read MoreZTE Launches ZXCSec MAF security solution for large model
A multi-layered security framework protecting large-model applications from adversarial threats, data leakage, API abuse, and content risks
Partner Content At MWC Shanghai 2025, ZTE has officially launched its ZXCSec MAF product, a dedicated application-layer security protection device specifically designed for large model services.…
Read MoreGoogle links Android’s Quick Share to Apple’s AirDrop, without Cupertino’s help
Relies on very loose permissions, but don’t worry – Google wrote it in Rust
Google has linked Android’s wireless peer-to-peer file sharing tool Quick Share to Apple’s equivalent AirDrop.…
Read MoreSEC drops SolarWinds lawsuit that painted a target on CISOs everywhere
Company 'clearly delighted' with the outcome
The US Securities and Exchange Commission (SEC) has abandoned the lawsuit it pursued against SolarWinds and its chief infosec officer for misleading investors about security practices that led to the 2020 SUNBURST attack.…
Read MoreSalesforce-linked data breach claims 200+ victims, has ShinyHunters’ fingerprints all over it
They keep coming back for more
Salesforce has disclosed another third-party breach in which criminals - likely ShinyHunters (again) - may have accessed hundreds of its customers' data.…
Read MoreLLM-generated malware is improving, but don't expect autonomous attacks tomorrow
Researchers tried to get ChatGPT to do evil, but it didn't do a good job
LLMs are getting better at writing malware - but they're still not ready for prime time.…
Read MoreFired techie admits sabotaging ex-employer, causing $862K in damage
PowerShell script locked thousands of workers out of their accounts
An Ohio IT contractor has pleaded guilty to breaking into his former employer's systems and causing nearly $1 million worth of damage after being fired.…
Read MoreTP-Link accuses rival Netgear of 'smear campaign' over alleged China ties
Networking vendor claims rival helped portray it as a national-security risk in the US
TP-Link is suing rival networking vendor Netgear, alleging that the rival and its CEO carried out a smear campaign by falsely suggesting, it says, that the biz had been infiltrated by the Chinese government.…
Read MoreEducation boards left gates wide open for PowerSchool mega-breach, say watchdogs
Privacy cops say attack wasn't just bad luck but a result of sloppy homework
Canadian privacy watchdogs say that school boards must shoulder part of the blame for the PowerSchool mega-breach, not just the ed-tech giant that lost control of millions of student and staff records.…
Read MorePalo Alto kit sees massive surge in malicious activity amid mystery traffic flood
GlobalProtect login endpoints targeted, sparking concern that something bigger may be brewing
Malicious traffic targeting Palo Alto Networks' GlobalProtect portals surged almost 40-fold in the space of 24 hours, hitting a 90-day high and putting defenders on alert for whatever comes next.…
Read MorePalo Alto CEO tips nation-states to weaponize quantum computing by 2029
Company thinks you’ll contemplate replacing most security kit in the next few years to stay safe
Palo Alto Networks CEO Nikesh Arora has suggested hostile nation-states will possess quantum computers in 2029, or even a little earlier, at which point most security appliances will need to be replaced.…
Read MoreUS, UK, Australia sanction Lockbit gang’s hosting provider
‘Bulletproof’ hosts partly dodged the last attack of this sort
Cybercrime fighters in the US, UK, and Australia have imposed sanctions on several Russia-linked entities they claim provide hosting services to ransomware gangs Lockbit, BlackSuit, and Play.…
Read MoreFortinet 'fesses up to second 0-day within a week
Attackers may be joining the dots to enable unauthenticated RCE
Fortinet has confirmed that another flaw in its FortiWeb web application firewall has been exploited as a zero-day and issued a patch, just days after disclosing a critical bug in the same product that attackers had found and abused a month earlier.…
Read MoreAmazon security boss: Hostile countries use cyber targeting for physical military strikes
And companies are getting caught in the crossfire
interview Warfare has become a joint cyber-kinetic endeavor, with nations using cyber operations to scope out targets before launching missiles. And private companies, including shipping, transportation, and electronics manufacturers, are getting caught in the crossfire, according to Amazon.…
Read MoreResearchers claim 'largest leak ever' after uncovering WhatsApp enumeration flaw
Two-day exploit opened up 3.5 billion users to myriad potential harms
Researchers in Austria used a flaw in WhatsApp to gather the personal data of more than 3.5 billion users in what they believe amounts to the "largest data leak in history."…
Read MoreTens of thousands more ASUS routers pwned by suspected, evolving China operation
Researchers say attacks are laying the groundwork for stealthy espionage activity
Around 50,000 ASUS routers have been compromised in a sophisticated attack that researchers believe may be linked to China, according to findings released today by SecurityScorecard's STRIKE team.…
Read MoreSelling technology investments to the board: a strategic guide for CISOs and CIOs
The C-suite will have zero interest in zero trust without a good business case
Partner Content In today's enterprise environment, technology investments are no longer judged solely by their technical sophistication. Approval depends on their ability to support business goals, mitigate risk, and create value for shareholders. CIOs and CISOs are expected to present their strategies not as technical upgrades but as business enablers. The challenge is not just making the right investments, but framing them in ways that resonate at the boardroom level.…
Read MoreChina recruiting spies in the UK with fake headhunters and ‘sites like LinkedIn’
MI5 sounds the alarm about attempts to source sensitive information
Chinese spies are using social media and fake recruitment agents to recruit sources with access to sensitive information in the UK.…
Read MoreSelf-replicating botnet attacks Ray clusters
Using AI to attack AI
updated Malefactors are actively attacking internet-facing Ray clusters and abusing the open source AI framework to spread a self-replicating botnet that mines for cryptocurrency, steals data, and launches distributed denial of service (DDoS) attacks.…
Read MoreFCC looks to torch Biden-era cyber rules sparked by Salt Typhoon mess
Regulator sides with telcos that claimed new cybersecurity duties were too ‘burdensome’
The Federal Communications Commission (FCC) will vote this week on whether to scrap Biden-era cybersecurity rules, enacted after the Salt Typhoon attacks came to light in 2024, that required telecom carriers to adopt basic security controls.…
Read MoreTake fight to the enemy, US cyber boss says
When? Sean Cairncross wouldn't say
America is fed up with being the prime target for foreign hackers. So US National Cyber Director Sean Cairncross says Uncle Sam is going on the offensive – he just isn't saying when.…
Read MoreGoogle Chrome bug exploited as an 0-day - patch now or risk full system compromise
Seventh Chrome 0-day this year
Google pushed an emergency patch on Monday for a high-severity Chrome bug that attackers have already found and exploited in the wild.…
Read MoreZoomers are officially worse at passwords than 80-year-olds
They can probably set up a printer faster, but look elsewhere for cryptography advice
Gen Z can get off their digital high horses because their passwords are no more secure than their grandparents'.…
Read More'Largest-ever' cloud DDoS attack pummels Azure with 3.64B packets per second
Aisuru botnet strikes again, bigger and badder
Azure was hit by the "largest-ever" cloud-based distributed denial of service (DDoS) attack, originating from the Aisuru botnet and measuring 15.72 terabits per second (Tbps), according to Microsoft.…
Read MorePentagon and soldiers let too many secrets slip on social networks, watchdog says
Ready, aim, mire
Loose lips sink ships, the classic line goes. Information proliferation in the internet age has government auditors reiterating that loose tweets can sink fleets, and they're concerned that the Defense Department isn't doing enough to stop sensitive info from getting out there. …
Read MoreSecurity researcher calls BS on Coinbase breach disclosure timeline
Claims he reported the attack in January after fraudsters tried to scam him
A security researcher says Coinbase knew about a December 2024 security breach during which miscreants bribed its support staff into handing over almost 70,000 customers' details at least four months before it disclosed the data theft.…
Read MoreSelling your identity to North Korean IT scammers isn't a sustainable side hustle
Four US citizens tried it, and the DoJ just secured guilty pleas from all of 'em
It sounds like easy money. North Koreans pay you to use your identity so they can get jobs working for American companies in IT. However, if you go this route, the US Department of Justice promises to catch up with you eventually.…
Read MoreGame over: Europol storms gaming platforms in extremist content sweep
Law enforcement agency’s referral blitz hit gaming platforms hard, surfacing thousands of extremist URLs
Europol's Internet Referral Unit (EU IRU) says a November 13 operation across gaming and "gaming-adjacent" services led its partners to report thousands of URLs hosting terrorist and hate-fueled material, including 5,408 links to jihadist content, 1,070 pushing violent right-wing extremist or terrorist propaganda, and 105 tied to racist or xenophobic groups.…
Read MoreOverconfidence is the new zero-day as teams stumble through cyber simulations
Readiness metrics have flatlined since 2023, with most sectors slipping backward as teams fumble crisis drills
Teams that think they're ready for a major cyber incident are scoring barely 22 percent accuracy and taking more than a day to contain simulated attacks, according to new data out Monday.…
Read MoreEurofiber admits crooks swiped data from French unit after cyberattack
Regulator reports suggest telco was extorted, but company remains coy as to whether it paid
French telco Eurofiber says cybercriminals swiped company data during an attack last week that also affected some internal systems.…
Read MoreUK prosecutors seize £4.11M in crypto from Twitter mega-hack culprit
Civil recovery order targets PlugwalkJoe's illicit gains while he serves US sentence
British prosecutors have secured a civil recovery order to seize crypto assets worth £4.11 million ($5.39 million) from Twitter hacker Joseph James O'Connor, clawing back the proceeds of a scam that used hijacked celebrity accounts to solicit digital currency and threaten high-profile individuals.…
Read MoreJaguar Land Rover hack cost India's Tata Motors around $2.4 billion and counting
PLUS: Active noise cancellation for entire rooms; More trouble for Korea Telecom; The Wiggles apologize for bad batteries; and more
Asia In Brief India’s Tata Motors, owner of Jaguar Land Rover, has revealed the cyberattack that shut down production in the UK has so far cost it around £1.8 billion ($2.35 billion).…
Read MoreLogitech leaks data after zero-day attack
PLUS: CISA still sitting on telecoms security report; DoorDash phished again; Lumma stealer returns; and more
INFOSEC IN BRIEF The US Senate passed a resolution in July to force the US Cybersecurity and Infrastructure Security Agency (CISA) to publish a 2022 report into poor security in the telecommunications industry but the agency has not delivered the document.…
Read MoreFortinet finally cops to critical make-me-admin bug under active exploitation
More than a month after PoC made public
Fortinet finally published a security advisory on Friday for a critical FortiWeb path traversal vulnerability under active exploitation – but it appears digital intruders got a month's head start.…
Read MoreCrims poison 150K+ npm packages with token-farming malware
Amazon spilled the TEA
Yet another supply chain attack has hit the npm registry in what Amazon describes as "one of the largest package flooding incidents in open source registry history" - but with a twist. Instead of injecting credential-stealing code or ransomware into the packages, this one is a token farming campaign.…
Read MoreFBI flags scam targeting Chinese speakers with bogus surgery bills
Crooks spoof US insurers, threaten bogus extradition to pry loose personal data and cash
Chinese speakers in the US are being targeted as part of an aggressive health insurance scam campaign, the FBI warns.…
Read MoreCISA flags imminent threat as Akira ransomware starts hitting Nutanix AHV
Advisory updated as leading cybercrime crew opens up its target pool
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued new guidance to organizations on the Akira ransomware operation, which poses an imminent threat to critical sectors.…
Read MoreClop claims it hacked 'the NHS.' Which bit? Your guess is as good as theirs
Cybercrime crew has ravaged multiple private organizations using Oracle EBS zero-day for months
The UK's National Health Service (NHS) is investigating claims of a cyberattack by extortion crew Clop.…
Read MoreKubernetes overlords decide Ingress NGINX isn’t worth saving
Maintenance to end next year after ‘helpful options’ became ‘serious security flaws’
Kubernetes maintainers have decided it’s not worth trying to save Ingress NGINX and will instead stop work on the project and retire it in March 2026.…
Read MoreChinese spies told Claude to break into about 30 critical orgs. Some attacks succeeded
Anthropic dubs this the first AI-orchestrated cyber snooping campaign
Chinese cyber spies used Anthropic's Claude Code AI tool to attempt digital break-ins at about 30 high-profile companies and government organizations – and the government-backed snoops "succeeded in a small number of cases," according to a Thursday report from the AI company.…
Read MoreRansomed CTO falls on sword, refuses to pay extortion demand
Checkout.com will instead donate the amount to fund cybercrime research
Digitial extortion is a huge business, because affected orgs keep forking over money to get their data back. However, instead of paying a ransom demand after getting hit by extortionists last week, payment services provider Checkout.com donated the demanded amount to fund cybercrime research.…
Read MoreUbuntu 25.10's Rusty sudo holes quickly welded shut
The goal of 'oxidizing' the Linux distro hits another bump
Two vulnerabilities in Ubuntu 25.10's new "sudo-rs" command have been found, disclosed, and fixed in short order.…
Read MoreExtra, extra, read all about it: Washington Post clobbered in Clop caper
Nearly 10,000 staff and contractors warned after attackers raided newspaper's Oracle EBS setup
The Washington Post has confirmed that nearly 10,000 employees and contractors had sensitive personal data stolen in the Clop-linked Oracle E-Business Suite (EBS) attacks.…
Read MoreRhadamanthys malware admin rattled as cops seize a thousand-plus servers
Operation Endgame also takes down Elysium and VenomRAT infrastructure
International cops have pulled apart the Rhadamanthys infostealer operation, seizing 1,025 servers tied to the malware in coordinated raids between November 10-13.…
Read MoreNHS supplier ends probe into ransomware attack that contributed to patient death
Synnovis's 18-month forensic review of Qilin intrusion completed, now affected patients to be notified
Synnovis has finally wrapped up its investigation into the 2024 ransomware attack that crippled pathology services across London, ending an 18-month effort to untangle what the NHS supplier describes as one of the most complex data reconstruction jobs it has ever faced.…
Read MoreGoogle sues 25 China-based scammers behind Lighthouse 'phishing for dummies' kit
600+ phishing websites and 116 of these use a Google logo
Google has filed a lawsuit against 25 unnamed China-based scammers, which it claims have stolen more than 115 million credit card numbers in the US as part of the Lighthouse phishing operation.…
Read MoreAttackers turned Citrix, Cisco 0-day exploits into custom-malware hellscape
Vendors (still) keep mum
An "advanced" attacker exploited CitrixBleed 2 and a max-severity Cisco Identity Services Engine (ISE) bug as zero-days to deploy custom malware, according to Amazon Chief Information Security Officer CJ Moses.…
Read MoreBitcoin bandit's £5B bubble bursts as cops wrap seven-year chase
Metropolitan Police lands lengthy sentence following 'complex' investigation
The Metropolitan Police's seven-year investigation into a record-setting fraudster has ended after she was sentenced to 11 years and eight months in prison on Tuesday.…
Read MoreCybercriminals Exploit Browser Push Notifications to Deliver Malware
Researchers at BlackFrog have uncovered Matrix Push C2, a malicious command-and-control system that abuses web browser push notifications to deliver malware
Read MoreNew Gainsight Supply Chain Hack Could Affect Salesforce Customers
Salesforce believes there has been unauthorized access to its customers’ data through the Gainsight app’s connection to its platform
Read MoreUNC2891 Money Mule Network Reveals Full Scope of ATM Fraud Operation
A multi-year ATM fraud campaign by UNC2891 targeted two Indonesian banks, cloning cards, recruiting money mules and coordinating cash withdrawals
Read MoreCISA Issues New Guidance on Bulletproof Hosting Threat
CISA launches guide to combat cybercrime via bulletproof hosting, recommending measures for ISPs
Read MoreSupply Chain Breaches Impact Almost All Firms Globally, BlueVoyant Reveals
Despite a growing maturity of third-party risk management programs, supply chain attacks impacted more organizations in 2025 than in previous years
Read MoreGartner: 40% of Firms to Be Hit By Shadow AI Security Incidents
Gartner predicts that two-fifths of organizations will suffer security and compliance incidents due to shadow AI by 2030
Read MoreUK, US and Australia Sanction Russian Bulletproof Hoster Media Land
Allies sanction bulletproof hoster Media Land and four executives
Read MoreEuropol Operation Disrupts $55m in Cryptocurrency For Piracy
Europe-wide Cyber-Patrol Week targeted IP violations, flagging 69 sites and disrupting $55m in crypto services
Read MoreEternidade Stealer Trojan Fuels Aggressive Brazil Cybercrime
Trustwave SpiderLabs has observed new banking Trojan Eternidade Stealer targeting Brazil using WhatsApp for propagation and data theft
Read MorePlushDaemon Hackers Unleash New Malware in China-Aligned Spy Campaigns
The cyber espionage group uses a previously undocumented network implant to drop two downloaders, LittleDaemon and DaemonLogistics, which deliver a backdoor
Read MoreChina-Linked Operation “WrtHug” Hijacks Thousands of ASUS Routers
SecurityScorecard has revealed a new Chinese campaign targeting thousands of ASUS routers globally
Read MoreHalf of Ransomware Access Due to Hijacked VPN Credentials
Beazley Security data finds the top cause of initial access for ransomware in Q3 was compromised VPN credentials
Read MoreWeek in review: Stealth-patched FortiWeb vulnerability under active exploitation, Logitech data breach
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: The tech that turns supply chains from brittle to unbreakable In this Help Net Security interview, Sev Kelian, CISO and VP of Security at Tecsys, discusses how organizations can strengthen supply chain resilience through a more unified and forward-looking strategy. Kelian also shares how new technologies and a blended view of cyber and physical risk are changing the way teams … More
The post Week in review: Stealth-patched FortiWeb vulnerability under active exploitation, Logitech data breach appeared first on Help Net Security.
Read MoreSalesforce Gainsight compromise: Early findings and customer guidance
In the wake of Salesforce’s announcement about “unusual activity involving Gainsight-published applications” and the company’s revocation of access and refresh tokens associated with them, Gainsight has been doing a good job keeping customers updated on current investigation findings. On the status page following the incident, the company confirmed that, as a precautionary measure, the Gainsight app has been temporarily pulled from the Hubspot Marketplace and Zendesk connector access has been revoked. They have also shared … More
The post Salesforce Gainsight compromise: Early findings and customer guidance appeared first on Help Net Security.
Read MoreNew Onapsis platform updates enhance visibility and protection across SAP landscapes
Onapsis introduced a series of new updates to its Onapsis Control product line, advancing security capabilities across SAP and cloud ERP application development environments. These enhancements include integration with SAP Continuous Integration and Delivery (CI/CD), expanded Git repository support to secure more code at rest, and strengthened workflow integration with SAP Transport Management System (TMS). Onapsis also expanded support for SAP Web Dispatcher and SAP Cloud Connector within the Onapsis Assess and Onapsis Defend product … More
The post New Onapsis platform updates enhance visibility and protection across SAP landscapes appeared first on Help Net Security.
Read MoreResearch shows identity document checks are missing key signals
Most CISOs spend their time thinking about account takeover and phishing, but identity document fraud is becoming a tougher challenge. A new systematic review shows how attackers are pushing past old defenses and how detection models are struggling to keep up. The study analyzes work published from 2020 to 2025, giving security leaders a view of where these systems stand and what is holding them back. A detection problem shaped by data limits The researchers … More
The post Research shows identity document checks are missing key signals appeared first on Help Net Security.
Read MoreWhat insurers really look at in your identity controls
Insurers judge organizations by the strength of their identity controls and by how consistently those controls are applied, according to a new Delinea report. CISOs are entering a market that rewards maturity and penalizes gaps that once passed without scrutiny. Control maturity is the baseline for insurability Nearly all security leaders said they were required to have at least some security controls in place before coverage was approved. Insurers expect organizations to show progress in … More
The post What insurers really look at in your identity controls appeared first on Help Net Security.
Read MoreHow one quick AI check can leak your company’s secrets
In this Help Net Security video, Dinesh Nagarajan, Global Partner, Cyber Security Services at IBM Consulting, walks through a situation in which an employee shared production source code with a public AI tool. The tool learned from the code, including special formulas used in a fintech app, which created the risk that similar answers could later be given to other users. The video shows how this kind of action can weaken a company’s position and … More
The post How one quick AI check can leak your company’s secrets appeared first on Help Net Security.
Read MoreConvenience culture is breaking personal security
AI is changing how scams are built, shared, and trusted. A new global survey from Bitdefender shows how far the problem has spread. AI is helping scams evolve faster than people can respond Over seven in ten consumers encountered some form of scam in the past year. One in seven fell for one. Worry about AI driven fraud is now mainstream, with 37% listing deepfake audio and video as their top concern. AI tools let … More
The post Convenience culture is breaking personal security appeared first on Help Net Security.
Read MoreNew infosec products of the week: November 21, 2025
Here’s a look at the most interesting products from the past week, featuring releases from Bedrock Data, Immersive, Kentik, Minimus, and Synack. Kentik AI Advisor brings intelligence and automation to network design and operations Kentik has launched the Kentik AI Advisor, an agentic AI solution that understands enterprise and service provider networks, thinks critically, and offers guidance for designing, operating, and protecting infrastructure at scale. Bedrock Data expands platform with AI governance and natural-language policy … More
The post New infosec products of the week: November 21, 2025 appeared first on Help Net Security.
Read MoreSalesforce investigates new incident echoing Salesloft Drift compromise
In what may be a repeat of the Salesloft Drift supply chain compromise, Salesforce confirmed that they’ve identified unusual activity involving Gainsight-published apps connected to Salesforce. “Our investigation indicates this activity may have enabled unauthorized access to certain customers’ Salesforce data through the app’s connection. Upon detecting the activity, Salesforce revoked all active access and refresh tokens associated with Gainsight-published applications connected to Salesforce and temporarily removed those applications from the AppExchange while our investigation … More
The post Salesforce investigates new incident echoing Salesloft Drift compromise appeared first on Help Net Security.
Read MoreSecurity gap in Perplexity’s Comet browser exposed users to system-level attacks
There is a serious security problem inside Comet, the AI-powered agentic browser made by Perplexity, SquareX researchers say: Comet’s MCP API allows the browser’s built-in (but hidden from the user) extensions to issue commands directly to a user’s device, and the capability can be leveraged by attackers. Comet can run applications, read files and modify data on the local system. “Old-school” browsers normally block this level of access, but (some) AI-powered browsers are effectively braking … More
The post Security gap in Perplexity’s Comet browser exposed users to system-level attacks appeared first on Help Net Security.
Read MoreThe OSINT playbook: Find your weak spots before attackers do
Here’s how open-source intelligence helps trace your digital footprint and uncover your weak points, plus a few essential tools to connect the dots
Read MorePlushDaemon compromises network devices for adversary-in-the-middle attacks
ESET researchers have discovered a network implant used by the China-aligned PlushDaemon APT group to perform adversary-in-the-middle attacks
Read MoreWhat if your romantic AI chatbot can’t keep a secret?
Does your chatbot know too much? Here's why you should think twice before you tell your AI companion everything.
Read MoreHow password managers can be hacked – and how to stay safe
Look no further to learn how cybercriminals could try to crack your vault and how you can keep your logins safe
Read MoreWhy shadow AI could be your biggest security blind spot
From unintentional data leakage to buggy code, here’s why you should care about unsanctioned AI use in your company
Read MoreIn memoriam: David Harley
Former colleagues and friends remember the cybersecurity researcher, author, and mentor whose work bridged the human and technical sides of security
Read MoreThe who, where, and how of APT attacks in Q2 2025–Q3 2025
ESET Chief Security Evangelist Tony Anscombe highlights some of the key findings from the latest issue of the ESET APT Activity Report
Read MoreESET APT Activity Report Q2 2025–Q3 2025
An overview of the activities of selected APT groups investigated and analyzed by ESET Research in Q2 2025 and Q3 2025
Read MoreSharing is scaring: The WhatsApp screen-sharing scam you didn’t see coming
How a fast-growing scam is tricking WhatsApp users into revealing their most sensitive financial and other data
Read MoreHow social engineering works | Unlocked 403 cybersecurity podcast (S2E6)
Think you could never fall for an online scam? Think again. Here's how scammers could exploit psychology to deceive you – and what you can do to stay one step ahead
Read MoreGround zero: 5 things to do after discovering a cyberattack
When every minute counts, preparation and precision can mean the difference between disruption and disaster
Read MoreThis month in security with Tony Anscombe – October 2025 edition
From the end of Windows 10 support to scams on TikTok and state-aligned hackers wielding AI, October's headlines offer a glimpse of what's shaping cybersecurity right now
Read MoreFraud prevention: How to help older family members avoid scams
Families that combine open communication with effective behavioral and technical safeguards can cut the risk dramatically
Read MoreCybersecurity Awareness Month 2025: When seeing isn't believing
Deepfakes are blurring the line between real and fake and fraudsters are cashing in, using synthetic media for all manner of scams
Read MoreRecruitment red flags: Can you spot a spy posing as a job seeker?
Here’s what to know about a recent spin on an insider threat – fake North Korean IT workers infiltrating western firms
Read MoreHow MDR can give MSPs the edge in a competitive market
With cybersecurity talent in short supply and threats evolving fast, managed detection and response is emerging as a strategic necessity for MSPs
Read MoreCybersecurity Awareness Month 2025: Cyber-risk thrives in the shadows
Shadow IT leaves organizations exposed to cyberattacks and raises the risk of data loss and compliance failures
Read MoreGotta fly: Lazarus targets the UAV sector
ESET research analyzes a recent instance of the Operation DreamJob cyberespionage campaign conducted by Lazarus, a North Korea-aligned APT group
Read MoreSnakeStealer: How it preys on personal data – and how you can protect yourself
Here’s what to know about the malware with an insatiable appetite for valuable data, so much so that it tops this year's infostealer detection charts
Read MoreCybersecurity Awareness Month 2025: Building resilience against ransomware
Ransomware rages on and no organization is too small to be targeted by cyber-extortionists. How can your business protect itself against the threat?
Read MoreMinecraft mods: Should you 'hack' your game?
Some Minecraft mods don’t help build worlds – they break them. Here’s how malware can masquerade as a Minecraft mod.
Read MoreIT service desks: The security blind spot that may put your business at risk
Could a simple call to the helpdesk enable threat actors to bypass your security controls? Here’s how your team can close a growing security gap.
Read MoreCybersecurity Awareness Month 2025: Why software patching matters more than ever
As the number of software vulnerabilities continues to increase, delaying or skipping security updates could cost your business dearly.
Read MoreAI-aided malvertising: Exploiting a chatbot to spread scams
Cybercriminals have tricked X’s AI chatbot into promoting phishing scams in a technique that has been nicknamed “Grokking”. Here’s what to know about it.
Read MoreHow Uber seems to know where you are – even with restricted location permissions
Is the ride-hailing app secretly tracking you? Not really, but this iOS feature may make it feel that way.
Read MoreCybersecurity Awareness Month 2025: Passwords alone are not enough
Never rely on just a password, however strong it may be. Multi-factor authentication is essential for anyone who wants to protect their online accounts from intruders.
Read MoreThe case for cybersecurity: Why successful businesses are built on protection
Company leaders need to recognize the gravity of cyber risk, turn awareness into action, and put security front and center
Read MoreBeware of threats lurking in booby-trapped PDF files
Looks can be deceiving, so much so that the familiar icon could mask malware designed to steal your data and money.
Read MoreManufacturing under fire: Strengthening cyber-defenses amid surging threats
Manufacturers operate in one of the most unforgiving threat environments and face a unique set of pressures that make attacks particularly damaging
Read MoreNew spyware campaigns target privacy-conscious Android users in the UAE
ESET researchers have discovered campaigns distributing spyware disguised as Android Signal and ToTok apps, targeting users in the United Arab Emirates
Read MoreCybersecurity Awareness Month 2025: Knowledge is power
We're kicking off the month with a focus on the human element: the first line of defense, but also the path of least resistance for many cybercriminals
Read MoreThis month in security with Tony Anscombe – September 2025 edition
The past 30 days have seen no shortage of new threats and incidents that brought into sharp relief the need for well-thought-out cyber-resilience plans
Read MoreRoblox executors: It’s all fun and games until someone gets hacked
You could be getting more than you bargained for when you download that cheat tool promising quick wins
Read MoreDeceptiveDevelopment: From primitive crypto theft to sophisticated AI-based deception
Malware operators collaborate with covert North Korean IT workers, posing a threat to both headhunters and job seekers
Read MoreWatch out for SVG files booby-trapped with malware
What you see is not always what you get as cybercriminals increasingly weaponize SVG files as delivery vectors for stealthy malware
Read MoreGamaredon X Turla collab
Notorious APT group Turla collaborates with Gamaredon, both FSB-associated groups, to compromise high‑profile targets in Ukraine
Read MoreSmall businesses, big targets: Protecting your business against ransomware
Long known to be a sweet spot for cybercriminals, small businesses are more likely to be victimized by ransomware than large enterprises
Read MoreHybridPetya: The Petya/NotPetya copycat comes with a twist
HybridPetya is the fourth publicly known real or proof-of-concept bootkit with UEFI Secure Boot bypass functionality
Read MoreIntroducing HybridPetya: Petya/NotPetya copycat with UEFI Secure Boot bypass
UEFI copycat of Petya/NotPetya exploiting CVE-2024-7344 discovered on VirusTotal
Read MoreAre cybercriminals hacking your systems – or just logging in?
As bad actors often simply waltz through companies’ digital front doors with a key, here’s how to keep your own door locked tight
Read MorePreventing business disruption and building cyber-resilience with MDR
Given the serious financial and reputational risks of incidents that grind business to a halt, organizations need to prioritize a prevention-first cybersecurity strategy
Read MoreUnder lock and key: Safeguarding business data with encryption
As the attack surface expands and the threat landscape grows more complex, it’s time to consider whether your data protection strategy is fit for purpose
Read MoreGhostRedirector poisons Windows servers: Backdoors with a side of Potatoes
ESET researchers have identified a new threat actor targeting Windows servers with a passive C++ backdoor and a malicious IIS module that manipulates Google search results
Read MoreThis month in security with Tony Anscombe – August 2025 edition
From Meta shutting down millions of WhatsApp accounts linked to scam centers all the way to attacks at water facilities in Europe, August 2025 saw no shortage of impactful cybersecurity news
Read MoreDon’t let “back to school” become “back to (cyber)bullying”
Cyberbullying is a fact of life in our digital-centric society, but there are ways to push back
Read MoreFirst known AI-powered ransomware uncovered by ESET Research
The discovery of PromptLock shows how malicious use of AI models could supercharge ransomware and other threats
Read More"What happens online stays online" and other cyberbullying myths, debunked
Separating truth from fiction is the first step towards making better parenting decisions. Let’s puncture some of the most common misconceptions about online harassment.
Read MoreThe need for speed: Why organizations are turning to rapid, trustworthy MDR
How top-tier managed detection and response (MDR) can help organizations stay ahead of increasingly agile and determined adversaries
Read MoreInvestors beware: AI-powered financial scams swamp social media
Can you tell the difference between legitimate marketing and deepfake scam ads? It’s not always as easy as you may think.
Read MoreSupply-chain dependencies: Check your resilience blind spot
Does your business truly understand its dependencies, and how to mitigate the risks posed by an attack on them?
Read MoreHow the always-on generation can level up its cybersecurity game
Digital natives are comfortable with technology, but may be more exposed to online scams and other threats than they think
Read MoreWinRAR zero-day exploited in espionage attacks against high-value targets
The attacks used spearphishing campaigns to target financial, manufacturing, defense, and logistics companies in Europe and Canada, ESET research finds
Read MoreUpdate WinRAR tools now: RomCom and others exploiting zero-day vulnerability
ESET Research discovered a zero-day vulnerability in WinRAR being exploited in the wild in the guise of job application documents; the weaponized archives exploited a path traversal flaw to compromise their targets
Read MoreBlack Hat USA 2025: Is a high cyber insurance premium about your risk, or your insurer’s?
A sky-high premium may not always reflect your company’s security posture
Read MoreAndroid adware: What is it, and how do I get it off my device?
Is your phone suddenly flooded with aggressive ads, slowing down performance or leading to unusual app behavior? Here’s what to do.
Read MoreBlack Hat USA 2025: Policy compliance and the myth of the silver bullet
Who’s to blame when the AI tool managing a company’s compliance status gets it wrong?
Read MoreBlack Hat USA 2025: Does successful cybersecurity today increase cyber-risk tomorrow?
Success in cybersecurity is when nothing happens, plus other standout themes from two of the event’s keynotes
Read MoreESET Threat Report H1 2025: ClickFix, infostealer disruptions, and ransomware deathmatch
Threat actors are embracing ClickFix, ransomware gangs are turning on each other – toppling even the leaders – and law enforcement is disrupting one infostealer after another
Read MoreIs your phone spying on you? | Unlocked 403 cybersecurity podcast (S2E5)
Here's what you need to know about the inner workings of modern spyware and how to stay away from apps that know too much
Read MoreWhy the tech industry needs to stand firm on preserving end-to-end encryption
Restricting end-to-end encryption on a single-country basis would not only be absurdly difficult to enforce, but it would also fail to deter criminal activity
Read MoreThis month in security with Tony Anscombe – July 2025 edition
Here's a look at cybersecurity stories that moved the needle, raised the alarm, or offered vital lessons in July 2025
Read MoreThe hidden risks of browser extensions – and how to stay safe
Not all browser add-ons are handy helpers – some may contain far more than you have bargained for
Read MoreSharePoint under fire: ToolShell attacks hit organizations worldwide
The ToolShell bugs are being exploited by cybercriminals and APT groups alike, with the US on the receiving end of 13 percent of all attacks
Read MoreToolShell: An all-you-can-eat buffet for threat actors
ESET Research has been monitoring attacks involving the recently discovered ToolShell zero-day vulnerabilities
Read MoreRogue CAPTCHAs: Look out for phony verification pages spreading malware
Before rushing to prove that you're not a robot, be wary of deceptive human verification pages as an increasingly popular vector for delivering malware
Read MoreWhy is your data worth so much? | Unlocked 403 cybersecurity podcast (S2E4)
Behind every free online service, there's a price being paid. Learn why your digital footprint is so valuable, and when you might actually be the product.
Read MoreUnmasking AsyncRAT: Navigating the labyrinth of forks
ESET researchers map out the labyrinthine relationships among the vast hierarchy of AsyncRAT variants
Read MoreHow to get into cybersecurity | Unlocked 403 cybersecurity podcast (S2E3)
Cracking the code of a successful cybersecurity career starts here. Hear from ESET's Robert Lipovsky as he reveals how to break into and thrive in this fast-paced field.
Read MoreTask scams: Why you should never pay to get paid
Some schemes might sound unbelievable, but they’re easier to fall for than you think. Here’s how to avoid getting played by gamified job scams.
Read MoreHow government cyber cuts will affect you and your business
Deep cuts in cybersecurity spending risk creating ripple effects that will put many organizations at a higher risk of falling victim to cyberattacks
Read MoreGamaredon in 2024: Cranking out spearphishing campaigns against Ukraine with an evolved toolset
ESET Research analyzes Gamaredon’s updated cyberespionage toolset, new stealth-focused techniques, and aggressive spearphishing operations observed throughout 2024
Read MoreESET Threat Report H1 2025: Key findings
ESET Chief Security Evangelist Tony Anscombe looks at some of the report's standout findings and their implications for organizations in 2025
Read MoreESET APT Activity Report Q4 2024–Q1 2025: Malware sharing, wipers and exploits
ESET experts discuss Sandworm’s new data wiper, relentless campaigns by UnsolicitedBooker, attribution challenges amid tool-sharing, and other key findings from the latest APT Activity Report
Read MoreThis month in security with Tony Anscombe – June 2025 edition
From Australia's new ransomware payment disclosure rules to another record-breaking DDoS attack, June 2025 saw no shortage of interesting cybersecurity news
Read MoreESET Threat Report H1 2025
A view of the H1 2025 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and research experts
Read MoreBladedFeline: Whispering in the dark
ESET researchers analyzed a cyberespionage campaign conducted by BladedFeline, an Iran-aligned APT group with likely ties to OilRig
Read MoreDon’t let dormant accounts become a doorway for cybercriminals
Do you have online accounts you haven't used in years? If so, a bit of digital spring cleaning might be in order.
Read MoreThis month in security with Tony Anscombe – May 2025 edition
From a flurry of attacks targeting UK retailers to campaigns corralling end-of-life routers into botnets, it's a wrap on another month filled with impactful cybersecurity news
Read MoreWord to the wise: Beware of fake Docusign emails
Cybercriminals impersonate the trusted e-signature brand and send fake Docusign notifications to trick people into giving away their personal or corporate data
Read MoreDanabot under the microscope
ESET Research has been tracking Danabot’s activity since 2018 as part of a global effort that resulted in a major disruption of the malware’s infrastructure
Read MoreDanabot: Analyzing a fallen empire
ESET Research shares its findings on the workings of Danabot, an infostealer recently disrupted in a multinational law enforcement operation
Read MoreLumma Stealer: Down for the count
The bustling cybercrime enterprise has been dealt a significant blow in a global operation that relied on the expertise of ESET and other technology companies
Read MoreESET takes part in global operation to disrupt Lumma Stealer
Our intense monitoring of tens of thousands of malicious samples helped this global disruption operation
Read MoreThe who, where, and how of APT attacks in Q4 2024–Q1 2025
ESET Chief Security Evangelist Tony Anscombe highlights key findings from the latest issue of the ESET APT Activity Report
Read MoreESET APT Activity Report Q4 2024–Q1 2025
An overview of the activities of selected APT groups investigated and analyzed by ESET Research in Q4 2024 and Q1 2025
Read MoreSednit abuses XSS flaws to hit gov't entities, defense companies
Operation RoundPress targets webmail software to steal secrets from email accounts belonging mainly to governmental organizations in Ukraine and defense contractors in the EU
Read MoreOperation RoundPress
ESET researchers uncover a Russia-aligned espionage operation targeting webmail servers via XSS vulnerabilities
Read MoreHow can we counter online disinformation? | Unlocked 403 cybersecurity podcast (S2E2)
Ever wondered why a lie can spread faster than the truth? Tune in for an insightful look at disinformation and how we can fight one of the most pressing challenges facing our digital world.
Read MoreCatching a phish with many faces
Here’s a brief dive into the murky waters of shape-shifting attacks that leverage dedicated phishing kits to auto-generate customized login pages on the fly
Read MoreBeware of phone scams demanding money for ‘missed jury duty’
When we get the call, it’s our legal responsibility to attend jury service. But sometimes that call won’t come from the courts – it will be a scammer.
Read MoreToll road scams are in overdrive: Here’s how to protect yourself
Have you received a text message about an unpaid road toll? Make sure you’re not the next victim of a smishing scam.
Read MoreRSAC 2025 wrap-up – Week in security with Tony Anscombe
From the power of collaborative defense to identity security and AI, catch up on the event's key themes and discussions
Read MoreTheWizards APT group uses SLAAC spoofing to perform adversary-in-the-middle attacks
ESET researchers analyzed Spellbinder, a lateral movement tool used to perform adversary-in-the-middle attacks
Read MoreThis month in security with Tony Anscombe – April 2025 edition
From the near-demise of MITRE's CVE program to a report showing that AI outperforms elite red teamers in spearphishing, April 2025 was another whirlwind month in cybersecurity
Read MoreHow safe and secure is your iPhone really?
Your iPhone isn't necessarily as invulnerable to security threats as you may think. Here are the key dangers to watch out for and how to harden your device against bad actors.
Read MoreDeepfake 'doctors' take to TikTok to peddle bogus cures
Look out for AI-generated 'TikDocs' who exploit the public's trust in the medical profession to drive sales of sketchy supplements
Read MoreHow fraudsters abuse Google Forms to spread scams
The form and quiz-building tool is a popular vector for social engineering and malware. Here’s how to stay safe.
Read MoreWill super-smart AI be attacking us anytime soon?
What practical AI attacks exist today? “More than zero” is the answer – and they’re getting better.
Read MoreCapCut copycats are on the prowl
Cybercriminals lure content creators with promises of cutting-edge AI wizardry, only to attempt to steal their data or hijack their devices instead
Read MoreThey’re coming for your data: What are infostealers and how do I stay safe?
Here's what to know about malware that raids email accounts, web browsers, crypto wallets, and more – all in a quest for your sensitive data
Read MoreWhen AI Goes Rogue, Science Fiction Meets Reality
The new movie Tron: Ares isn’t just sci-fi entertainment — it’s a mirror for today’s AI risks and realities. What happens when artificial intelligence systems don't work as intended?
The post When AI Goes Rogue, Science Fiction Meets Reality appeared first on Security Boulevard.
Read MoreCloudflare Outage: Should You Go Multi-CDN?
As a DDoS testing and resilience consultancy, we routinely advise our clients to strengthen their architecture by using a reputable CDN like Cloudflare. After this week’s Cloudflare outage, however, many organizations are understandably asking themselves a new question: Should we adopt a multi-CDN strategy instead of relying on a single provider? For the vast majority […]
The post Cloudflare Outage: Should You Go Multi-CDN? appeared first on Security Boulevard.
Read MoreU.S., International Partners Target Bulletproof Hosting Services

Agencies with the US and other countries have gone hard after bulletproof hosting services providers this month, including Media Land, Hypercore, and associated companies and individuals, while the FiveEyes threat intelligence alliance published BPH mitigation guidelines for ISPs, cloud providers, and network defenders.
The post U.S., International Partners Target Bulletproof Hosting Services appeared first on Security Boulevard.
Read MoreWhat makes a Agentic AI solution scalable?
How Can Non-Human Identities Enhance Scalable AI Solutions? Have you ever considered the role Non-Human Identities (NHIs) play in enhancing scalable AI solutions? With the increasing reliance on technology, particularly in the cloud, managing NHIs is crucial for security and efficiency. Understanding NHIs involves knowing their components—machine identities and the secrets they hold—which are essential […]
The post What makes a Agentic AI solution scalable? appeared first on Entro.
The post What makes a Agentic AI solution scalable? appeared first on Security Boulevard.
Read MoreHow do Non-Human Identities keep my data protected?
Can Better Management of Non-Human Identities Safeguard Your Cloud Data? Do organizations truly understand the importance of managing Non-Human Identities (NHIs) and their secrets? While we navigate the complex seas of digital transformation, machine identities, commonly known as NHIs, have become vital. These identities, much like digital passports, facilitate communication between systems. Yet, they can […]
The post How do Non-Human Identities keep my data protected? appeared first on Entro.
The post How do Non-Human Identities keep my data protected? appeared first on Security Boulevard.
Read MoreAre current Non-Human Identities impenetrable?
How Secure Are Your Non-Human Identities? Is your organization effectively managing the security of its Non-Human Identities (NHIs)? Where companies continue to transition to digital environments, the complexity of maintaining robust cybersecurity measures has increased exponentially. The need for secure NHI management is crucial, especially for sectors like financial services, healthcare, and DevOps. But what […]
The post Are current Non-Human Identities impenetrable? appeared first on Entro.
The post Are current Non-Human Identities impenetrable? appeared first on Security Boulevard.
Read MoreSalesforce: Some Customer Data Accessed via Gainsight Breach

An attack on the app of CRM platform-provider Gainsight led to the data of hundreds of Salesforce customers being compromised, highlighting the ongoing threats posed by third-party software in SaaS environments and illustrating how one data breach can lead to others, cybersecurity pros say.
The post Salesforce: Some Customer Data Accessed via Gainsight Breach appeared first on Security Boulevard.
Read MoreSaturday Security: Zero-Day Logitech Breach Exposes 1.8TB of Data
Logitech, a prominent PC accessories brand, has recently confirmed a major data breach after cybercriminals exploited a zero-day vulnerability in a third-party platform. While Logitech assures that exposed data was limited and credit card numbers, as well as national IDs, were not stored on the impacted systems, the situation remains concerning. The notorious Clop ransomware […]
The post Saturday Security: Zero-Day Logitech Breach Exposes 1.8TB of Data appeared first on Security Boulevard.
Read MoreNDSS 2025 – Explanation As A Watermark
SESSION
Session 3D: AI Safety
-----------
-----------
Authors, Creators & Presenters: Shuo Shao (Zhejiang University), Yiming Li (Zhejiang University), Hongwei Yao (Zhejiang University), Yiling He (Zhejiang University), Zhan Qin (Zhejiang University), Kui Ren (Zhejiang University)
-----------
PAPER
Explanation as a Watermark: Towards Harmless and Multi-bit Model Ownership Verification via Watermarking Feature Attribution
Ownership verification is currently the most critical and widely adopted post-hoc method to safeguard model copyright. In general, model owners exploit it to identify whether a given suspicious third-party model is stolen from them by examining whether it has particular properties 'inherited' from their released models. Currently, backdoor-based model watermarks are the primary and cutting-edge methods to implant such properties in the released models. However, backdoor-based methods have two fatal drawbacks, including harmfulness and ambiguity. The former indicates that they introduce maliciously controllable misclassification behaviors ( backdoor) to the watermarked released models. The latter denotes that malicious users can easily pass the verification by finding other misclassified samples, leading to ownership ambiguity.
In this paper, we argue that both limitations stem from the 'zero-bit' nature of existing watermarking schemes, where they exploit the status (misclassified) of predictions for verification. Motivated by this understanding, we design a new watermarking paradigm "Explanation as a Watermark (EaaW)", that implants verification behaviors into the explanation of feature attribution instead of model predictions. Specifically, EaaW embeds a 'multi-bit' watermark into the feature attribution explanation of specific trigger samples without changing the original prediction. We correspondingly design the watermark embedding and extraction algorithms inspired by explainable artificial intelligence. In particular, our approach can be used for different tasks (image classification and text generation). Extensive experiments verify the effectiveness and harmlessness of our EaaW and its resistance to potential attacks.
-----------
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – Explanation As A Watermark appeared first on Security Boulevard.
Read MoreMaking A Cyber Crisis Plan! Key Components Not To Be Missed
Do you think cyberattacks are headlines anymore? Given the frequent occurrences, it has turned headlines into a day-to-day reality, and that’s scarier! Organizations that are big names to small organizations that are still growing, every one of them is being hit one way or the other. From supply chain attacks to data breaches, the impact […]
The post Making A Cyber Crisis Plan! Key Components Not To Be Missed appeared first on Kratikal Blogs.
The post Making A Cyber Crisis Plan! Key Components Not To Be Missed appeared first on Security Boulevard.
Read MoreIberia discloses customer data leak after vendor security breach
Spanish flag carrier Iberia has begun notifying customers of a data security incident stemming from a compromise at one of its suppliers. The disclosure comes days after a threat actor claimed on hacker forums to have access to 77 GB of data allegedly stolen from the airline. [...]
Read MoreNew Costco Gold Star Members also get a $40 Digital Costco Shop Card*
The holidays can be hard on any budget, but there may be a way to make it a little easier. Instead of dashing through the snow all around town, get all your shopping done under one roof at Costco. Right now, you can even get a 1-Year Costco Gold Star Membership plus a $40 Digital Costco Shop Card*, and it's still only $65. [...]
Read MoreWhatsApp API flaw let researchers scrape 3.5 billion accounts
Researchers compiled a list of 3.5 billion WhatsApp mobile phone numbers and associated personal information by abusing a contact-discovery API that lacked rate limiting. [...]
Read MoreCox Enterprises discloses Oracle E-Business Suite data breach
Cox Enterprises is notifying impacted individuals of a data breach that exposed their personal data to hackers who breached the company network after exploiting a zero-day flaw in Oracle E-Business Suite. [...]
Read MorePiecing Together the Puzzle: A Qilin Ransomware Investigation
Huntress analysts reconstructed a Qilin ransomware attack from a single endpoint, using limited logs to reveal rogue ScreenConnect access, failed infostealer attempts, and the ransomware execution path. The investigation shows how validating multiple data sources can uncover activity even when visibility is reduced to a "pinhole." [...]
Read MoreCISA warns Oracle Identity Manager RCE flaw is being actively exploited
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning government agencies to patch an Oracle Identity Manager tracked as CVE-2025-61757 that has been exploited in attacks, potentially as a zero-day. [...]
Read MoreNvidia confirms October Windows updates cause gaming issues
Nvidia has confirmed that last month's security updates are causing gaming performance issues on Windows 11 24H2 and Windows 11 25H2 systems. [...]
Read MoreMicrosoft: Out-of-band update fixes Windows 11 hotpatch install loop
Microsoft has released an out-of-band cumulative update to fix a known issue causing the November 2025 KB5068966 hotpatch update to reinstall on Windows 11 systems repeatedly. [...]
Read MoreGrafana warns of max severity admin spoofing vulnerability
Grafana Labs is warning of a maximum severity vulnerability (CVE-2025-41115) in its Enterprise product that can be exploited to treat new users as administrators or for privilege escalation. [...]
Read MoreCrowdStrike catches insider feeding information to hackers
American cybersecurity firm CrowdStrike has confirmed that an insider shared screenshots taken on internal systems with hackers after they were leaked on Telegram by the Scattered Lapsus$ Hunters threat actors. [...]
Read MoreFCC rolls back cybersecurity rules for telcos, despite state-hacking risks
The Federal Communications Commission (FCC) has rolled back a previous ruling that required U.S. telecom carriers to implement stricter cybersecurity measures following the massive hack from the Chinese threat group known as Salt Typhoon. [...]
Read More'Scattered Spider' teens plead not guilty to UK transport hack
Two British teenagers have denied charges related to an investigation into the breach of Transport for London (TfL) in August 2024, which caused millions of pounds in damage and exposed customer data. [...]
Read MoreAvast Makes AI-Driven Scam Defense Available for Free Worldwide
Avast is rolling out Scam Guardian, a free AI-powered protection layer that analyzes websites, messages, and links to detect rising scam threats. Powered by Gen Threat Labs data, it reveals hidden dangers in code and adds 24/7 scam guidance through the Avast Assistant. [...]
Read MoreGoogle begins showing ads in AI Mode (AI answers)
Google has started rolling out ads in AI mode, which is the company's "answer engine," not a search engine. [...]
Read MoreSecurity startup Guardio nabs $80M from ION Crossover Partners
Guardio is leveraging its experience building browser extensions and apps that scan for malicious and phishing sites to build a tool that looks for artifacts in code and websites made with vibe-coding tools.
Read MoreGoogle now lets you add friends as contacts for account recovery
Google now lets you recover your accounts using your phone number or trusted contacts.
Read MoreCyber giant F5 Networks says government hackers had ‘long-term’ access to its systems, stole code and customer data
The company, which provides cybersecurity defenses to most of the Fortune 500, said the DOJ allowed it to delay notifying the public on national security grounds.
Read MoreA breach every month raises doubts about South Korea’s digital defenses
Known for its blazing fast internet and home to some of the world’s biggest tech giants, South Korea has also faced a string of data breaches and cybersecurity lapses that has struggled to match the pace of its digital ambitions.
Read MoreProton releases a new app for two-factor authentication
Proton has a free authenticator app, which is available cross-platform with end-to-end encryption protection for data.
Read MoreKnox lands $6.5M to compete with Palantir in the federal compliance market
Irina Denisenko, CEO of Knox, launched Knox, a federal managed cloud provider, last year with a mission to help software vendors speed through the FedRAMP security authorization process in just three months, and at a fraction of what it would cost to do it on their own.
Read MoreGoogle is adding new device-level features for its Advanced Protection program
At the Android Show, taking place ahead of Google I/O 2025, Google announced that it is adding new device-specific features to its Advanced Protection program, which is designed to protect public figures such as politicians and journalists from different digital threats, with the Android 16 release. The new features include a new way of storing […]
Read MoreGoogle announces new security features for Android for protection against scam and theft
At the Android Show on Tuesday, ahead of Google I/O, Google announced new security and privacy features for Android. These new features include new protections for calls, screen sharing, messages, device access, and system-level permissions. With these features, Google aims to protect users from falling for a scam, keep their details secure in case a […]
Read MoreA 25-year-old police drone founder just raised $75M led by Index
If you ever call 911 from an area that’s hard to get to, you might hear the buzz of a drone well before a police cruiser pulls up. And there’s a good chance that it will be one made by Brinc Drones, a Seattle-based startup founded by 25-year-old Blake Resnick, who dropped out of college […]
Read MoreA new security fund opens up to help protect the fediverse
A new security fund aims to help apps in the fediverse — like Mastodon, Threads, and Pixelfed — to pay researchers for disclosing security bugs.
Read MoreHow to tell if your online accounts have been hacked
This is a guide on how to check whether someone compromised your online accounts.
Read MoreHackers are ramping up attacks using year-old ServiceNow security bugs to target unpatched systems
Threat intelligence startup GreyNoise says it has observed a ‘notable resurgence’ in attack activity
Read MoreUS teachers’ union says hackers stole sensitive personal data on over 500,000 members
PSEA says it "took steps to ensure" its stolen data was deleted, suggesting a ransom demand was paid
Read MoreCISA scrambles to contact fired employees after court rules layoffs ‘unlawful’
Federal court rules U.S. cybersecurity agency must re-hire over 100 former employees
Read MoreDOGE axes CISA ‘red team’ staffers amid ongoing federal cuts
Affected staff say more than 100 employees working to protect U.S. government networks were ‘axed’ with no prior warning
Read MoreWhat PowerSchool won’t say about its data breach affecting millions of students
New details have emerged about PowerSchool's data breach — but here's what PowerSchool still isn't saying.
Read MoreHacker accessed PowerSchool’s network months before massive December breach
CrowdStrike says a hacker had access to PowerSchool's internal system as far back as August.
Read MoreJapanese telco giant NTT Com says hackers accessed details of almost 18,000 organizations
Unidentified hackers breached NTT Com’s network to steal personal information of employees at thousands of corporate customers
Read MoreFBI says scammers are targeting US executives with fake BianLian ransom notes
The FBI is warning that scammers are impersonating the BianLian ransomware gang using fake ransom notes sent to U.S. corporate executives. The fake ransom notes, first reported by U.S. cybersecurity company GuidePoint Security, claim that hackers have gained access to an organization’s network to steal sensitive data, and threaten to publish the stolen data unless […]
Read MoreUK quietly scrubs encryption advice from government websites
The UK is no longer recommending the use of encryption for at-risk groups following its iCloud backdoor demands
Read MoreWhat Lessons Can We Learn from the Cloudflare Outage on November 18, 2025?
The November 18, 2025 outage will be remembered as one of the most significant infrastructure incidents of the past decade. Within minutes, thousands of websites and applications worldwide faced 5xx errors, severe slowdowns, or complete unavailability. Behind this global disruption was a widespread failure at Cloudflare, one of the central pillars of today’s Internet. This … Continue reading What Lessons Can We Learn from the Cloudflare Outage on November 18, 2025?
The post What Lessons Can We Learn from the Cloudflare Outage on November 18, 2025? appeared first on KoDDoS Blog.
Read MoreCloudflare is down !!!
Massive internet outage: Cloudflare incident brings part of the global web to a standstill A major outage hit Cloudflare this afternoon, rendering numerous websites and online services inaccessible. From X to Feedly, including Marmiton and Doctissimo, users are reporting loading errors, inaccessible pages, and massive slowdowns. The exact cause of the malfunction remains unknown at … Continue reading Cloudflare is down !!!
The post Cloudflare is down !!! appeared first on KoDDoS Blog.
Read MoreKoDDoS was in Paris yesterday for Tech Show Paris 2025
Barely back from Miami where CloudFest 2025 was held, our teams were yesterday in Paris for Tech Show Paris 2025 a key European gathering where strategic vision, technological innovation and real operational feedback truly intersect. Tech Show Paris is one of the most influential events in Europe for cloud, cybersecurity, data and infrastructure professionals. The … Continue reading KoDDoS was in Paris yesterday for Tech Show Paris 2025
The post KoDDoS was in Paris yesterday for Tech Show Paris 2025 appeared first on KoDDoS Blog.
Read MoreKoDDoS at CloudFest USA in Miami
KoDDoS is currently on-site at CloudFest USA in Miami. CloudFest USA is recognized as the most strategic event for the internet infrastructure, cloud hosting, and digital sovereignty ecosystem. Here in Miami, industry leaders gather to shape the next phase of the Internet: business models, network architecture, cybersecurity, resilience, independence and trust. Miami itself is symbolic: … Continue reading KoDDoS at CloudFest USA in Miami
The post KoDDoS at CloudFest USA in Miami appeared first on KoDDoS Blog.
Read MoreKoDDoS, MSP Global and CloudFest: a Strategic Partnership for the Future of the Cloud
KoDDoS is proud to announce its partnership with MSP Global and CloudFest, two key players in the digital technology and cloud services industry. This collaboration marks an important step toward strengthening ties within the global tech ecosystem, bringing together experts, service providers, and decision-makers to address the cloud’s most strategic challenges. Through this partnership, we … Continue reading KoDDoS, MSP Global and CloudFest: a Strategic Partnership for the Future of the Cloud
The post KoDDoS, MSP Global and CloudFest: a Strategic Partnership for the Future of the Cloud appeared first on KoDDoS Blog.
Read MoreRecap of Our Presence at VivaTech 2025
Our Core Expertise: Offshore Hosting & Advanced Cybersecurity At KoDDoS, we’ve built our reputation on two complementary pillars: 🛡️ Robust Cybersecurity Capabilities For over a decade, we’ve been protecting digital infrastructure with cutting-edge security technologies: 🌐 Resilient and Sovereign Offshore Hosting Our global infrastructure is distributed across strategic offshore data centers in: This setup offers … Continue reading Recap of Our Presence at VivaTech 2025
The post Recap of Our Presence at VivaTech 2025 appeared first on KoDDoS Blog.
Read MoreKoDDoS at VivaTechnology 2025: A Strategic Presence at the Heart of Cybersecurity and AI Challenges.
Paris, June 2025 – From June 11 to 14, Paris will once again become the global epicenter of technological innovation with the return of VivaTechnology 2025, held at Paris Expo Porte de Versailles. Bringing together major tech companies, disruptive startups, global investors, and public institutions, the event stands out as a pivotal moment for the … Continue reading KoDDoS at VivaTechnology 2025: A Strategic Presence at the Heart of Cybersecurity and AI Challenges.
The post KoDDoS at VivaTechnology 2025: A Strategic Presence at the Heart of Cybersecurity and AI Challenges. appeared first on KoDDoS Blog.
Read MoreGamer Over? Why Hackers Target Popular Video Games & How to Stay Safe
Video games are more than entertainment; they’re a $200 billion global industry. But as gaming grows, so do cyberattacks. Hackers now see games as goldmines for stealing data, extorting companies, and exploiting players. According to Infosecurity Magazine, Akamai’s 2024 report shows that attacks on gaming platforms are rising alarmingly. In 2024 alone, the industry suffered … Continue reading Gamer Over? Why Hackers Target Popular Video Games & How to Stay Safe
The post Gamer Over? Why Hackers Target Popular Video Games & How to Stay Safe appeared first on KoDDoS Blog.
Read MoreHow Social Media Use Can Create Hidden Cybersecurity Risks
Social media is all around us, helping us stay connected, updated, and entertained. But beneath the endless scroll, a darker reality exists. Hidden cybersecurity threats are growing- some obvious, others much harder to spot. The risks are especially alarming for young users. According to the National Institutes of Health, up to 95% of teens aged … Continue reading How Social Media Use Can Create Hidden Cybersecurity Risks
The post How Social Media Use Can Create Hidden Cybersecurity Risks appeared first on KoDDoS Blog.
Read MoreKoDDoS at the InCyber Europe 2025 Forum: a strategic participation at the heart of the European cyber ecosystem
From April 1st to 3rd, 2025, KoDDoS, a provider of specialized services in DDoS protection and secure offshore hosting, marked its presence at the InCyber Europe Forum, held at the Lille Grand Palais. A true crossroads of cyber innovation and cooperation, the event is the largest cybersecurity event in Europe. A benchmark event on an … Continue reading KoDDoS at the InCyber Europe 2025 Forum: a strategic participation at the heart of the European cyber ecosystem
The post KoDDoS at the InCyber Europe 2025 Forum: a strategic participation at the heart of the European cyber ecosystem appeared first on KoDDoS Blog.
Read MoreWhat Did We Learn from the NCSC’s 2025 Annual Review?
Earlier this year, the UK’s National Cyber Security Centre (NCSC) released its annual review for 2025. The report reveals the troubling reality of the modern threat landscape and, crucially, how the NCSC recommends organizations and the wider security ecosystem shield themselves from it. Let’s dive in. Incident Frequency Has Stagnated, Incident Severity Has Skyrocketed The number of incidents for which the NCSC provided support has remained largely unchanged. The severity of those incidents, however, has skyrocketed. The NCSC sorts all incidents into one of three categories: Category 1...
Read MoreThe Hidden Cost of Oversharing: How Your Social Posts Fuel Doxxing Campaigns
Many don’t question what they share online. Others think, what could possibly happen? The answer: “plenty.” We all leave traces. A birthday photo here, a check-in there, a proud post about a promotion. None of it seems dangerous on its own, but online, fragments add up. Each click, tag, or comment starts to paint a fuller picture: one more detailed than most of us know, or would like. Throw in a few leaked datasets, an exposed broker record, and a social media trail, and anyone with time and patience can patch together a surprisingly accurate profile. That’s how doxxing, or the gathering and...
Read MoreThe UK’s Four-Step Framework for Supply Chain Resilience
Ransomware attacks can ripple through supply chains, causing serious disruption and massive financial consequences for multiple businesses in one fell swoop. As such, CISOs are spending more time considering how to keep operations secure as ecosystems span across dozens, if not hundreds, of vendors, contractors, and digital dependencies. With this in mind, the UK government has released a strategic framework to help organizations secure their supply chains. Let’s explore that guidance. Step 1: Understand why supply chain security is important Your security is only as strong as the weakest...
Read MoreSecurity vs. Compliance: What's the Difference?
Security and compliance—a phrase often uttered in the same breath as if they are two sides of the same coin, two members of the same team, or two great tastes that go great together. The truth is, they can be. But it takes some effort. How can security and compliance teams work together to create a winning alliance, protect data, develop according to modern practices, and still pass an audit? This blog will give you a start. A Real-World Scenario of Compliance and Security Living Two Separate Lives As much as I would like to see auditors, developers, and security analysts living in harmony...
Read MoreContinuous PCI DSS Compliance with File Integrity Monitoring
PCI DSS compliance is often seen as a one-off task, that is, you do the audit, implement controls, and then move on. But then there comes the problem - systems aren’t static, meaning that files, scripts, and configurations change constantly, and even small untracked changes can create gaps that lead to non-compliance or security issues. This is where File Integrity Monitoring (FIM) comes in. It tracks critical files, system binaries, scripts, and configs in real time, alerting when anything changes unexpectedly. For PCI DSS, this is exactly what’s required, from preventing unauthorized changes...
Read MoreAre We Failing to Secure Files? Attackers Aren’t Failing to Check
According to a new Ponemon study, weak file protections now account for several cybersecurity incidents a year for many organizations. Unsafe file-sharing practices, malicious vendor files, weak access controls, and obscured file activity are largely to blame. File Integrity Monitoring (FIM) could be the solution. Are Files Safe in Transit? More Than Half Unsure You know something’s wrong when more people feel better about downloading files from unknown sources than they do about file uploads or transfers. Over 50% were unsure if files sent via email, transferred via third parties, or...
Read MoreBeyond VDI: Security Patterns for BYOD and Contractors in 2025
Remote work is no longer a contingency – it’s the operating norm. Yet the security posture for that work often leans on virtual desktops as a default, even when the workforce is dominated by bring‑your‑own‑device (BYOD) users and short‑term contractors. Virtual desktop infrastructure (VDI) can centralize risk, but it can also centralize failure, expand the admin plane, and add latency that users will work around. This piece examines when VDI stops being the safest choice and what to use instead. I’ll compare concrete control patterns, such as secure local enclaves, strong identity guardrails...
Read MoreVulnerability Management and Patch Management: How They Work Together
Vulnerability management and patch management are often spoken of in the same breath. Yet they are not the same. Each serves a distinct purpose, and knowing the difference is more than a matter of semantics; it’s a matter of security. Confuse them, and gaps appear. Leave those gaps, and attackers will find them. To build a strong defense, you need to see how these two processes fit together. One scans the horizon for weaknesses. The other arms you with fixes. Both are vital, but neither can do the other’s job. Let’s take a closer look at what they mean, how they differ, and how they work in...
Read MoreUnderstanding the OWASP AI Maturity Assessment
Today, almost all organizations use AI in some way. But while it creates invaluable opportunities for innovation and efficiency, it also carries serious risks. Mitigating these risks and ensuring responsible AI adoption relies on mature AI models, guided by governance frameworks. The OWASP AI Maturity Assessment Model (AIMA) is one of the most practical. In this article, we’ll explore what it is, how it compares to other frameworks, and how organizations can use it to assess their AI maturity. What is the OWASP AI Maturity Assessment Model? The OWASP AI Maturity Assessment Model is a...
Read MoreCISOs Concerned of AI Adoption in Business Environments
UK security leaders are making their voices heard. Four in five want DeepSeek under regulation. They see a tool that promises efficiency but risks chaos. Business is already under pressure. Trade disputes drag on. Interest rates remain high. Cyber threats grow. Every move to expand operations adds risk, and risk is harder to measure when AI enters the equation. AI spreads fast. It cuts costs, fills gaps, and automates mundane tasks. But it also opens hidden doors. In the UK, AI is now part of daily work. A KPMG survey showed that while 69% of employees use it, only 42% trust it. Slightly over...
Read MoreCISA Issues Warning as Hackers Target Oracle Identity Manager RCE Flaw
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a new Oracle vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, warning that attackers are already exploiting it in real-world attacks. The bug, tracked as CVE-2025-61757, affects Oracle Identity Manager, part of Oracle Fusion Middleware. The flaw is rated as a “missing authentication for critical […]
The post CISA Issues Warning as Hackers Target Oracle Identity Manager RCE Flaw appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreHackers Use Salesforce Gainsight Breach to Access Data from More Than 200 Companies
Salesforce has disclosed a significant security incident involving unauthorized access to customer data through compromised Gainsight-published applications. The breach, detected in mid-November 2025, potentially exposed sensitive information from over 200 organizations that use the customer success platform integrated with Salesforce. Threat actors linked to the notorious ShinyHunters group exploited OAuth tokens to gain unauthorized access […]
The post Hackers Use Salesforce Gainsight Breach to Access Data from More Than 200 Companies appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreCrowdStrike Fires Employee for Leaking Internal System Info to Hackers
Cybersecurity giant CrowdStrike has terminated an employee who allegedly shared sensitive internal system information with a notorious hacking collective. The incident involved the leak of internal screenshots posted on a public Telegram channel operated by the threat group known as “Scattered Lapsus$ Hunters“. Insider Threat Detected Through Screen Sharing The leaked images displayed internal dashboards, […]
The post CrowdStrike Fires Employee for Leaking Internal System Info to Hackers appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreMetasploit Releases New Exploit for Fresh FortiWeb 0-Day Vulnerabilities
Rapid7’s Metasploit team has released a new exploit module targeting critical zero-day vulnerabilities in Fortinet’s FortiWeb web application firewall, chaining two security flaws to achieve unauthenticated remote code execution with root privileges. CVE ID Vulnerability Type Affected Product Impact CVE-2025-64446 Authentication Bypass Fortinet FortiWeb Administrative account creation, privilege escalation CVE-2025-58034 Command Injection Fortinet FortiWeb Remote […]
The post Metasploit Releases New Exploit for Fresh FortiWeb 0-Day Vulnerabilities appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreCritical Azure Bastion Vulnerability Lets Attackers Bypass Login and Escalate Privileges
A critical authentication bypass vulnerability in Azure Bastion, its managed remote access service, enables attackers to escalate privileges to administrative levels with a single network request. The vulnerability, designated CVE-2025-49752, affects all Azure Bastion deployments and received an emergency security patch on November 20, 2025. Attribute Details CVE ID CVE-2025-49752 Vulnerability Type Authentication Bypass / […]
The post Critical Azure Bastion Vulnerability Lets Attackers Bypass Login and Escalate Privileges appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreXillen Stealer: Advanced Features Bypass AI Detection and Steal Password Manager Data
The Python-based information-stealing tool Xillen Stealer has reached versions 4 and 5, significantly expanding its targeting capabilities and functionality across platforms. Documented initially by Cyfirma in September 2025, this cross-platform infostealer targets sensitive data, including credentials, cryptocurrency wallets, system information, and browser data, while employing sophisticated anti-analysis techniques to evade detection. The latest updates introduce […]
The post Xillen Stealer: Advanced Features Bypass AI Detection and Steal Password Manager Data appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreAI-Driven Obfuscated Malicious Apps Bypassing Antivirus Detection to Deliver Malicious Payloads
Cybersecurity researchers have identified a sophisticated malware campaign leveraging artificial intelligence to enhance obfuscation techniques, enabling malicious applications to circumvent traditional antivirus detection systems. The threat actors behind the campaign are distributing trojanized applications impersonating a prominent Korean delivery service, employing a multi-layered approach to evade security controls and maintain persistent command-and-control (C2) infrastructure. The […]
The post AI-Driven Obfuscated Malicious Apps Bypassing Antivirus Detection to Deliver Malicious Payloads appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreDark Web Job Market Evolved – Prioritizes Practical Skills Over Formal Education
The underground labor market has undergone a significant transformation. According to new research analyzing 2,225 job-related posts collected from shadow forums between January 2023 and June 2025. The dark web job market now emphasizes practical skills and real-world experience over traditional credentials, marking a notable shift from previous patterns and reflecting broader global employment trends. […]
The post Dark Web Job Market Evolved – Prioritizes Practical Skills Over Formal Education appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreNorth Korean Kimsuky and Lazarus Teams Target Critical Sectors with Zero-Day Exploits
North Korea’s two most formidable APT groups Kimsuky and Lazarus have established a coordinated operational framework that combines intelligence gathering with large-scale cryptocurrency theft. According to a comprehensive Trend Micro analysis, this collaboration poses an unprecedented threat to critical infrastructure worldwide, with attacks targeting the military, financial, blockchain, energy, and healthcare sectors across the United […]
The post North Korean Kimsuky and Lazarus Teams Target Critical Sectors with Zero-Day Exploits appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MoreWindows 11 to Prevent BSOD Error Messages from Showing Publicly
Microsoft has announced a significant Windows 11 update that will prevent the Blue Screen of Death (BSOD) and other system error messages from appearing on public-facing screens. The new feature, called Digital Signage mode, addresses a critical business continuity challenge faced by restaurants, airports, retail stores, and other organizations that rely on public displays. Digital Signage […]
The post Windows 11 to Prevent BSOD Error Messages from Showing Publicly appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
Read MorePrivacy group sues feds over talks with tech companies on ICE raid trackers
The lawsuit concerns the removal of apps like ICEBlock, Red Dot and DeICER from online playstores that provide real-time tracking of immigration raids.
The post Privacy group sues feds over talks with tech companies on ICE raid trackers appeared first on CyberScoop.
Read MoreLegacy web forms are the weakest link in government data security
Outdated government web forms are placing millions of citizens at risk as sensitive information is collected and transmitted through insecure, non-compliant systems.
The post Legacy web forms are the weakest link in government data security appeared first on CyberScoop.
Read MoreSEC drops case against SolarWinds tied to monumental breach
The Securities and Exchange Commission on Thursday dropped its case against SolarWinds and its chief information security officer over its handling of an alleged Russian cyberespionage campaign uncovered in 2020, an incident that penetrated at least nine federal agencies and hundreds of companies. The SEC’s decision brings to a halt one of the more divisive […]
The post SEC drops case against SolarWinds tied to monumental breach appeared first on CyberScoop.
Read MoreHundreds of Salesforce customers hit by yet another third-party vendor breach
The widespread compromise is strikingly similar to a previous attack that originated at Salesloft Drift.
The post Hundreds of Salesforce customers hit by yet another third-party vendor breach appeared first on CyberScoop.
Read MoreNSO Group argues WhatsApp injunction threatens existence, future U.S. government work
The spyware vendor made those two arguments, among others, in a motion to stay the California court ruling.
The post NSO Group argues WhatsApp injunction threatens existence, future U.S. government work appeared first on CyberScoop.
Read MoreTop Senate Intel Dem warns of ‘catastrophic’ cyber consequences of Trump admin national security firings, politicization
Sen. Mark Warner, D-Va., said the Trump administration is leaving the nation vulnerable at a time of rising threats in cyberspace.
The post Top Senate Intel Dem warns of ‘catastrophic’ cyber consequences of Trump admin national security firings, politicization appeared first on CyberScoop.
Read MoreWhy Anna Gomez believes the FCC is letting telecoms off easy after Salt Typhoon
Commissioner Gomez told CyberScoop the agency is poised to eliminate “the only meaningful regulatory response to Salt Typhoon that I have seen.”
The post Why Anna Gomez believes the FCC is letting telecoms off easy after Salt Typhoon appeared first on CyberScoop.
Read MorePalo Alto Networks to acquire observability firm Chronosphere for $3.35 billion
The cybersecurity giant's move into observability reflects how AI workloads are blurring lines between security and operations.
The post Palo Alto Networks to acquire observability firm Chronosphere for $3.35 billion appeared first on CyberScoop.
Read MoreFive Eyes just made life harder for bulletproof hosting providers
An international effort sanctioned Russia-based Media Land and took action against companies and people who helped Aeza Group evade previously issued sanctions.
The post Five Eyes just made life harder for bulletproof hosting providers appeared first on CyberScoop.
Read MoreAmazon warns of global rise in specialized cyber-enabled kinetic targeting
The company said the boundaries between cyber and physical attacks are dissolving as nation-states use network intrusions to aid military targeting in real time.
The post Amazon warns of global rise in specialized cyber-enabled kinetic targeting appeared first on CyberScoop.
Read MoreSECURITY AFFAIRS MALWARE NEWSLETTER ROUND 72
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malware Newsletter Contagious Interview Actors Now Utilize JSON Storage Services for Malware Delivery RONINGLOADER: DragonBreath’s New Path to PPL Abuse npm Malware Campaign Uses Adspect Cloaking to Deliver Malicious Redirects GPT Trade: Fake Google Play Store […]
Read MoreSecurity Affairs newsletter Round 551 by Pierluigi Paganini – INTERNATIONAL EDITION
A new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. BadAudio malware: how APT24 scaled its cyberespionage through supply chain attacks U.S. CISA adds an Oracle […]
Read MoreSonicWall flags SSLVPN flaw allowing firewall crashes
SonicWall warns of a high-severity buffer overflow flaw in SonicOS SSLVPN (CVE-2025-40601) that lets attackers crash Gen7 and Gen8 firewalls. A new high-severity SonicOS SSLVPN flaw, tracked as CVE-2025-40601 (CVSS score of 7.5), allows attackers to crash SonicWall Gen7 and Gen8 firewalls. SonicWall is urging all customers to apply patches immediately, as the issue stems […]
Read MoreBadAudio malware: how APT24 scaled its cyberespionage through supply chain attacks
APT24 used supply chain attacks and varied techniques to deploy the BadAudio malware in a long-running cyberespionage campaign. China-linked group APT24 used supply-chain attacks and multiple techniques over three years to deploy the BadAudio downloader and additional malware payloads, Google Threat Intelligence Group (GTIG) warns. According to the researchers, the group shifted from broad web […]
Read MoreU.S. CISA adds an Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities catalog
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds an Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a an Oracle Fusion Middleware flaw, tracked as CVE-2025-61757 (CVSS score of 9.8), to its Known Exploited Vulnerabilities (KEV) catalog. The vulnerability is a missing authentication for a critical function that […]
Read MoreCrowdStrike denies breach after insider sent internal screenshots to hackers
CrowdStrike says an insider shared internal screenshots with hackers but confirms no system breach and no customer data exposure. BleepingComputer first reported that CrowdStrike said an insider shared internal system screenshots with hackers, after Scattered Lapsus$ Hunters leaked them on Telegram. The company stresses that no systems were breached and no customer data was exposed. […]
Read MoreSolarWinds addressed three critical flaws in Serv-U
SolarWinds patched three critical vulnerabilities in its Serv-U file transfer solution that could allow remote code execution. SolarWinds addressed three critical vulnerabilities in its Serv-U file transfer solution that could allow remote code execution. The first vulnerability, tracked as CVE-2025-40549 (CVSS score 9.1), is a path restriction bypass issue that impacts Serv-U. An attacker with […]
Read MoreMassive data leak hits Italian railway operator Ferrovie dello Stato via Almaviva hack
Ferrovie dello Stato Italiane (FS) data leaked after a breach at IT provider Almaviva. A hacker claims the theft of 2.3 TB of sensitive data. Data belonging to Italy’s national railway operator Ferrovie dello Stato Italiane (FS) was leaked after a data breach at IT provider Almaviva. FS Italiane Group is Italy’s state-owned railway company, managing passenger […]
Read MoreSalesforce alerts users to potential data exposure via Gainsight OAuth apps
Salesforce warns that unusual activity in Gainsight-linked OAuth apps may have enabled unauthorized access to some customers’ Salesforce data. Salesforce warned of unusual activity involving Gainsight-linked OAuth apps, noting that threat actors may have used these integrations to gain unauthorized access to some customers’ Salesforce data. “Salesforce has identified unusual activity involving Gainsight-published applications connected […]
Read MoreResearchers devised a new enumeration technique that exposed 3.5B WhatsApp profiles
Researchers disclosed a WhatsApp flaw that exposed 3.5B accounts. Meta has patched it to prevent this mass enumeration. A team of researchers at the University of Vienna found a WhatsApp flaw that could scrape 3.5 billion accounts. Meta has since patched the vulnerability to block this enumeration technique. Users discover contacts by querying WhatsApp servers […]
Read MoreENISA becomes CVE Program Root, strengthening Europe’s vulnerability management framework
The European Union Agency for Cybersecurity (ENISA) has been officially designated as a Program Root in the global Common Vulnerabilities and Exposures (CVE) Program. It marks a significant step in the EU’s efforts to bolster cybersecurity resilience and streamline vulnerability coordination across member states. As a Program Root, ENISA will serve as the central point […]
The post ENISA becomes CVE Program Root, strengthening Europe’s vulnerability management framework appeared first on IT Security Guru.
Read MoreAPIContext Introduces MCP Server Performance Monitoring to Ensure Fast and Reliable AI Workflows
Today, APIContext, has launched its Model Context Protocol (MCP) Server Performance Monitoring tool, a new capability that ensures AI systems respond fast enough to meet customer expectations. Given that 85% of enterprises and 78% of SMBs are now using autonomous agents, MCP has emerged as the key enabler by providing an open standard that allows AI […]
The post APIContext Introduces MCP Server Performance Monitoring to Ensure Fast and Reliable AI Workflows appeared first on IT Security Guru.
Read MoreBridewell CEO gives cyber predictions for 2026
As global economic pressures increase and budgets across both public and private sectors are cut, Anthony Young, CEO at Bridewell, a company that provides cybersecurity services to CNI organisations, is warning of a critical inflection point for 2026, where organisations are facing more cyber threats with fewer resources to defend against them. According to Young, […]
The post Bridewell CEO gives cyber predictions for 2026 appeared first on IT Security Guru.
Read MoreSalt Security Launches GitHub Connect to Proactively Discover Shadow APIs and MCP Risks in Code Repositories
API security organisation Salt Security has announced the latest expansion of its innovative Salt Cloud Connect capability. It extends the same agentless model customers trust for rapidly gathering API-specific info in cloud platforms, applying the same proven ease of use and ‘under 10-minute’ deployment to GitHub source code. While other security solutions focus on AI […]
The post Salt Security Launches GitHub Connect to Proactively Discover Shadow APIs and MCP Risks in Code Repositories appeared first on IT Security Guru.
Read MoreKnowBe4 merges training content to create Studios
KnowBe4’s award-winning training content has now merged together under one umbrella, branded as KnowBe4 Studios. It will feature AI-forward training, fresh content, interactive games and expanded storytelling for an enhanced, immersive experience. KnowBe4’s content is among the highest rated in the industry, with an average rating of 4.6 out of 5 based on reviews from […]
The post KnowBe4 merges training content to create Studios appeared first on IT Security Guru.
Read MoreThe Quantum Future Is Coming – Hackers Are Already Preparing
In 2025 we’re not just fighting today’s headline-grabbing cyber threats, but we’re also preparing for tomorrow’s. Technology is evolving at a pace that is both fuelling progress for defenders and powering new tools for bad actors. The same advances that drive discovery and innovation also give cybercriminals new ways to attack faster, more broadly and […]
The post The Quantum Future Is Coming – Hackers Are Already Preparing appeared first on IT Security Guru.
Read MoreKeeper Security Unveils Secure Secrets Management in Visual Studio Code
Keeper Security has announced the launch of its Visual Studio Code (VS Code) extension, extending its enterprise-grade secrets management directly into developers’ coding environments. The VS Code extension expands the KeeperPAM® platform’s reach into the developer ecosystem, enabling secure, zero-trust secrets management throughout the software development lifecycle. Effective secrets management is vital for developers, as […]
The post Keeper Security Unveils Secure Secrets Management in Visual Studio Code appeared first on IT Security Guru.
Read MoreWhat Will Defense Contracting Look Like in 10 Years?
Global defense spending will reach $6.38 trillion by 2035, growing from $2.7 trillion in 2024 at a compound annual growth rate of 8.13%, according to Spherical Insights & Consulting research. This massive expansion coincides with fundamental shifts in how the U.S. government procures defense capabilities and manages contractor relationships. Margarita Howard, CEO and owner of […]
The post What Will Defense Contracting Look Like in 10 Years? appeared first on IT Security Guru.
Read MoreBlack Duck SCA Adds AI Model Scanning to Strengthen Software Supply Chain Security
Black Duck has expanded its software composition analysis (SCA) capabilities to include AI model scanning, helping organisations gain visibility into the growing use of open-source AI models embedded in enterprise software. With the release of version 2025.10.0, the company’s new AI Model Risk Insights capability allows teams to identify and analyse AI models used within […]
The post Black Duck SCA Adds AI Model Scanning to Strengthen Software Supply Chain Security appeared first on IT Security Guru.
Read MoreThe Increase In Adoption Of Video Surveillance-As-A-Service
The development of intelligently integrated, cloud-based management solutions has been a rising trend across major industries for many years. By centralising the collection, analysis and organisation of actionable data within remote-accessible, unified environments, leaders can streamline a wide variety of core processes and positively impact productivity metrics. These fundamental benefits underline the popularity of X-as-a-Service (XaaS) […]
The post The Increase In Adoption Of Video Surveillance-As-A-Service appeared first on IT Security Guru.
Read MoreLicense to Encrypt: “The Gentlemen” Make Their Move
Cybereason Threat Intelligence Team recently conducted an analysis of "The Gentlemen" ransomware group, which emerged around July 2025 as a ransomware threat actor group with relatively advanced methodologies. The Gentlemen group employs a dual-extortion strategy, not only encrypting sensitive files but also exfiltrating critical business data and threatening to publish it on dark web leak sites unless a ransom is paid. The group has demonstrated a unique approach by combining established ransomware techniques with newer strategies, making them quick to adapt to new attack vectors, allowing them to remain a persistent to evolving threat to organizations worldwide.
Read MoreTycoon 2FA Phishing Kit Analysis
The Tycoon 2FA phishing kit is a sophisticated Phishing-as-a-Service (PhaaS) platform that emerged in August 2023, designed to bypass two-factor authentication (2FA) and multi-factor authentication (MFA) protections, primarily targeting Microsoft 365 and Gmail accounts. Utilizing an Adversary-in-the-Middle (AiTM) approach, it employs a reverse proxy server to host deceptive phishing pages that mimic legitimate login interfaces, capturing user credentials and session cookies in real-time. According to the Any.run malware trends tracker, Tycoon 2FA leads with over 64,000 reported incidents this year.
Read MoreFrom Scripts to Systems: A Comprehensive Look at Tangerine Turkey Operations
Cybereason Security Services issue Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
In this Threat Analysis report, Cybereason Security Services investigates the flow of a Tangerine Turkey campaign observed in Cybereason EDR. Tangerine Turkey is a threat actor identified as a visual basic script (VBS) worm used to facilitate cryptomining activity.
Read MoreCybereason TTP Briefing Q3 2025: LOLBINs and CVE Exploits Dominate
Explore the latest trends, techniques, and procedures (TTPs) our incident response (IR) experts are actively facing with the TTP Briefing Q3 2025, a report built on frontline threat intelligence from our global incident response investigations, enriched by noteworthy detections from our SOC.
Read MoreAddressing CL0P Extortion Campaign Targeting Oracle EBS CVE-2025-61882
Overview and What Cybereason Knows So Far
- July 2025, Oracle releases security updates including 309 patches, which included nine that addressed flaws/vulnerabilities in Oracle E-Business Suite (EBS).
- July 2025 (end of) through September 2025 (beginning of), Cybereason has assessed based on emerging evidence and ongoing forensic investigations, that CL0P orchestrated an Intrusion Path that allowed for unauthorized access to on-premise, customer-managed Oracle E-Business Suite (EBS) solutions, enumerated accessible and stored data, and conducted data exfiltration.
- September 2025 (end of) through October 2025 (beginning of), a widespread orchestrated email extortion campaigns emerged targeting users of on-premise, customer-managed Oracle E-Business Suite (EBS) and requesting contact with CL0P in order to not expose data allegedly exfiltrated.
- October 2025 (beginning of), Cybereason is aware of ongoing investigations in which CL0P has provided proof of data. CL0P does not appear to have named new victims associated with this incident as of October 4, 2025.
- October 5, 2025, Oracle confirms CVE-2025-61882 in Oracle E-Business Suite (EBS). This vulnerability was remotely exploitable without authentication (i.e., it can be exploited over a network without the need for a username and password). Successful exploitation can lead to remote code execution (RCE).
- October 7, 2025, Cybereason confirms earliest evidence of threat actor activity occurred August 9, but is subject to change based on ongoing investigations.
7000+ IRs Later: The 11 Essential Cybersecurity Controls
Decades in incident response reveal battle-tested cybersecurity controls that minimize attack surface, improve detection and response, reduce incident impact and losses, and build cyber resilience (with compliance mappings for easy implementation).
Read MoreBehind the Mask of Madgicx Plus: A Chrome Extension Campaign Targeting Meta Advertisers
Cybereason Security Services recently analyzed an investigation into a broader malicious Chrome extension campaign, part of which had been previously documented by DomainTools. While earlier iterations of this campaign involved the impersonation a variety of services, the latest version shifts focus to Meta (Facebook/Instagram) advertisers through a newly crafted lure: “Madgicx Plus,” a fake AI-driven ad optimization platform. Promoted as a tool to streamline campaign management and boost ROI using artificial intelligence, the extension instead delivers potentially malicious functionalities capable of hijacking business sessions, stealing credentials, and compromising Meta Business accounts. Notably, several domains associated with earlier parts of the campaign have been repurposed to promote this new theme, highlighting the operators’ tendency to recycle infrastructure while adapting their social engineering strategy to new targets.
Read MoreCVE-2025-53770 & CVE-2025-53771: Critical On-Prem SharePoint Vulnerabilities
Key Takeaways
- Two zero-day vulnerabilities discovered in on-premise Microsoft SharePoint servers, tracked as CVE‑2025‑53770 and CVE‑2025‑53771.
- Affected versions include: Subscription Edition – KB5002768, SharePoint 2019 – KB5002754, SharePoint 2016 – KB5002760.
- If exploited, these vulnerabilities could allow for remote code execution (RCE).
- Cybereason has observed ongoing active exploitation attempts of these vulnerabilities through our Global SOC monitoring.
- With this exploit, we recommend taking an “assume compromised” posture, immediately patching impacted versions, and conducting incident response historical look back.
BlackSuit: A Hybrid Approach with Data Exfiltration and Encryption
Cybereason Security Services issue Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
Read MoreDeploying NetSupport RAT via WordPress & ClickFix
In May 2025, Cybereason Global Security Operations Center (GSOC) detected that threat actors have been hosting malicious WordPress websites to deliver malicious versions of the legitimate NetSupport Manager Remote Access Tool (RAT).
Read MoreHow to spot a holiday shopping scam: Fake deals, trick surveys & bogus gift cards
Scammers, fraudsters, and phishers take advantage of every season. But the holiday shopping season - which includes Black Friday, Cyber Monday, and Christmas - may be their favorite.
As retailers rush to capitalize on what is generally their most profitable time of year, they will generally flood email boxes with great offers that are often time sensitive and may even seem too-good-to-be-true. Meanwhile, consumers also feel the urgency to get their shopping done, along with the stresses of work and family. Add in the financial pressure of an inflationary economy and the likelihood of making a quick mistake keeps increasing. Read on for some simple yet effective ways to ruin the scammers' fun as you celebrate the season of giving.
Read MoreSoon�
Our "construction project" is progressing nicely.
And it should resolve this…
Fix mobile usability issues?
Translation: your site doesn't help us sell more Android phones and ads.
But whatever, the "issues" should be fixed soon enough.
On 18/08/15 At 12:52 PM
Read MoreWork In Progress
Regular readers will have noticed it's been slow here of late.
Under Construction
We're finally undertaking an upgrade from Greymatter 1.7.3. This may be the world's oldest Greymatter blog… that will now change.
More info coming soon.
In the meantime, you can still catch us on Twitter.
On 13/08/15 At 01:25 PM
Read More"IOS Crash Report" Update: Safari Adds Block Feature
Ask, and sometimes, you shall receive.
Last Friday, we wrote about call center scammers targeting iOS. And today, Apple released a new (beta) feature that should help.
Apple released iOS 9 Public Beta 2:
And it appears that one of Safari's new features allows people to block fraud-focused JavaScript.
We tested a scam-site and after a few attempts to dismiss the JavaScript dialog, Safari included a prompt to "Block Alerts". We were then easily able to close the page.
Kudos Apple! Looking forward to seeing this in iOS 9's general release.
Big hat tip to Rosyna Keller.
On 23/07/15 At 09:53 AM
Read MoreDuke APT group's latest tools: cloud services and Linux support
Recent weeks have seen the outing of two new additions to the Duke group's toolset, SeaDuke and CloudDuke. Of these, SeaDuke is a simple trojan made interesting by the fact that it's written in Python. And even more curiously, SeaDuke, with its built-in support for both Windows and Linux, is the first cross-platform malware we have observed from the Duke group. While SeaDuke is a single - albeit cross-platform - trojan, CloudDuke appears to be an entire toolset of malware components, or "solutions" as the Duke group apparently calls them. These components include a unique loader, downloader, and not one but two different trojan components. CloudDuke also greatly expands on the Duke group's usage of cloud storage services, specifically Microsoft's OneDrive, as a channel for both command and control as well as the exfiltration of stolen data. Finally, some of the recent CloudDuke spear-phishing campaigns have born a striking resemblance to CozyDuke spear-phishing campaigns from a year ago.
Linux support added with the cross-platform SeaDuke malware
Last week, both Symantec and Palo Alto Networks published research on SeaDuke, a newer addition to the arsenal of trojans being used by the Duke group. While older malware by the Duke group has always been written with a combination of the C and C++ programming languages as well as assembly language, SeaDuke is peculiarly written in Python with multiple layers of obfuscation. This Python code is usually then compiled into Windows executables using py2exe or pyinstaller. However, the Python code itself has been designed to work on both Windows and Linux. We therefore suspect, that the Duke group is also using the same SeaDuke Python code to target Linux victims. This is the first time we have seen the Duke group employ malware to target Linux platforms.
An example of the cross-platform support found in SeaDuke.
A new set of solutions with the CloudDuke malware toolset
Last week, we also saw Palo Alto Networks and Kaspersky Labs publish research on malware components they respectively called MiniDionis and CloudLook. MiniDionis and CloudLook are both components of a larger malware toolset we call CloudDuke. This toolset consists of malware components that provide varying functionality while partially relying on a shared code framework and always using the same loader. Based on PDB strings found in the samples, the malware authors refer to the CloudDuke components as "solutions" with names such as "DropperSolution", "BastionSolution" and "OneDriveSolution". A list of PDB strings we have observed is below:
� C:\DropperSolution\Droppers\Projects\Drop_v2\Release\Drop_v2.pdb
� c:\BastionSolution\Shells\Projects\miniDionis4\miniDionis\obj\Release\miniDionis.pdb
� c:\BastionSolution\Shells\Projects\miniDionis2\miniDionis\obj\Release\miniDionis.pdb
� c:\OneDriveSolution\Shells\Projects\OneDrive2\OneDrive\obj\x64\Release\OneDrive.pdb
The first of the CloudDuke components we have observed is a downloader internally called "DropperSolution". The purpose of the downloader is to download and execute additional malware on the victim's system. In most observed cases, the downloader will attempt to connect to a compromised website to download an encrypted malicious payload which the downloader will decrypt and execute. Depending on the way the downloader has been configured, in some cases it may first attempt to log in to Microsoft's cloud storage service OneDrive and retrieve the payload from there. If no payload is available from OneDrive, the downloader will revert to the previously mentioned method of downloading from compromised websites.
We have also observed two distinct trojan components in the CloudDuke toolset. The first of these, internally called "BastionSolution", is the trojan that Palo Alto Networks described in their research into "MiniDionis". Interestingly, BastionSolution appears to functionally be an exact copy of SeaDuke with the only real difference being the choice of programming language. BastionSolution also makes significant use of a code framework that is apparently internally called "Z". This framework provides classes for functionality such as encryption, compression, randomization and network communications.
A list of classes in the BastionSolution trojan, including multiple classes from the "Z" framework.
Classes from the same "Z" framework, such as the encryption and randomization classes, are also used by the second trojan component of the CloudDuke toolset. This second component, internally called "OneDriveSolution", is especially interesting because it relies on Microsoft's cloud storage service OneDrive as its command and control channel. To achieve this, OneDriveSolution will attempt to log into OneDrive with a preconfigured username and password. If successful, OneDriveSolution will then proceed to copy data from the victim's computer to the OneDrive account. It will also search the OneDrive account for files containing commands for the malware to execute.
A list of classes in the OneDriveSolution trojan, including multiple classes from the "Z" framework.
All of the CloudDuke "solutions" use the same loader, a piece of code whose primary purpose is to decrypt the embedded, encrypted solution, load it in memory and execute it. The Duke group has often employed loaders for their malware but unlike the previous loaders they have used, the CloudDuke loader is much more versatile with support for multiple methods of loading and executing the final payload as well as the ability to write to disk and execute additional malware components.
CloudDuke spear-phishing campaigns and similarities with CozyDuke
CloudDuke has recently been spread via spear-phishing emails with targets reportedly including organizations such as the US Department of Defense. These spear-phising emails have contained links to compromised websites hosting zip archives that contain CloudDuke-laden executables. In most cases, executing these executables will have resulted in two additional files being written to the victim's hard disk. The first of these files has been a decoy, such as an audio file or a PDF file while the second one has been a CloudDuke loader embedding a CloudDuke downloader, the so-called "DropperSolution". In these cases, the victim has been presented with the decoy file while in the background the downloader has proceeded to download and execute one of the CloudDuke trojans, "OneDriveSolution" or "BastionSolution".
Example of one of the decoy documents employed in the CloudDuke spear-phishing campaigns. It has apparently been copied by the attackers from here.
Interestingly, however, some of the other CloudDuke spear-phishing campaigns we have observed this July have born a striking resemblance to CozyDuke spear-phishing campaigns seen almost exactly a year ago, in the beginning of July 2014. In both spear-phishing campaigns, the decoy document has been the exact same PDF file, a "US letter fax test page" (28d29c702fdf3c16f27b33f3e32687dd82185e8b). Similarly, the URLs hosting the malicious files have, in both campaigns, purported to be related to eFaxes. It is also interesting to note, that in the case of the CozyDuke-inspired CloudDuke spear-phishing campaign, the downloading and execution of the malicious archive linked to in the emails has not resulted in the execution of the CloudDuke downloader but in the execution of the "BastionSolution" component thereby skipping one step from the process described for the other CloudDuke spear-phishing campaigns.
The "US letter fax test page" decoy employed in both CloudDuke and CozyDuke spear-phishing campaigns.
Increasingly using cloud services to evade detection
CloudDuke is not the first time we have observed the Duke group use cloud services in general and Microsoft OneDrive specifically as part of their operations. Earlier this spring we released research on CozyDuke where we mentioned observing CozyDuke sometimes either directly use a OneDrive account to exfiltrate stolen data or alternatively CozyDuke downloading Visual Basic scripts that would copy stolen files to a OneDrive account and sometimes even retrieve files containing additional commands from the same OneDrive account.
In these previous cases the Duke group has only used OneDrive as a secondary communication channel but still relied on more traditional C&C channels for most of their actions. It is therefore interesting to note that CloudDuke actually enables the Duke group to rely solely on OneDrive for every step of their operation from downloading the actual trojan, passing commands to the trojan and finally exfiltrating stolen data.
By relying solely on 3rd party web services, such as OneDrive, as their command and control channel, we believe the Duke group is trying to better evade detection. Large amounts of data being transferred from an organization's network to an unknown web server easily raises suspicions. However, data being transferred to a popular cloud storage service is normal. What better way for an attacker to surreptitiously transfer large amounts of stolen data than the same way people are transferring that same data every day for legitimate reasons. (Coincidentally, the implications of 3rd party web services being used as command and control channels is also the subject of an upcoming talk at the VirusBulletin 2015 conference).
Directing limited resources towards evading detection and staying ahead of defenders
Developing even a single multipurpose malware toolset, never mind many, requires time and resources. Therefore it seems logical to attempt to reuse code such as supporting frameworks between different toolsets. The Duke group, however, appear to have taken this a step further with SeaDuke and the CloudDuke component BastionSolution, by rewriting the same code in multiple programming languages. This has the obvious benefits of saving time and resources by providing two malware toolsets, that while similar on the inside, appear completely different on the outside. This way, the discovery of one toolset does not immediately lead to the discovery of the second toolset.
The Duke group, long suspected of ties to the Russian state, have been running their espionage operation for an unusually long time and - especially lately - with unusual brazenness. These latest CloudDuke and SeaDuke campaigns appear to be a clear sign that the Duke's are not planning to stop any time soon.
Research and post by Artturi (@lehtior2)
F-Secure detects CloudDuke as Trojan:W32/CloudDuke.B and Trojan:W64/CloudDuke.B
Samples:
04299c0b549d4a46154e0a754dda2bc9e43dff76
2f53bfcd2016d506674d0a05852318f9e8188ee1
317bde14307d8777d613280546f47dd0ce54f95b
476099ea132bf16fa96a5f618cb44f87446e3b02
4800d67ea326e6d037198abd3d95f4ed59449313
52d44e936388b77a0afdb21b099cf83ed6cbaa6f
6a3c2ad9919ad09ef6cdffc80940286814a0aa2c
78fbdfa6ba2b1e3c8537be48d9efc0c47f417f3c
9f5b46ee0591d3f942ccaa9c950a8bff94aa7a0f
bfe26837da22f21451f0416aa9d241f98ff1c0f8
c16529dbc2987be3ac628b9b413106e5749999ed
cc15924d37e36060faa405e5fa8f6ca15a3cace2
dea6e89e36cf5a4a216e324983cc0b8f6c58eaa8
e33e6346da14931735e73f544949a57377c6b4a0
ed0cf362c0a9de96ce49c841aa55997b4777b326
f54f4e46f5f933a96650ca5123a4c41e115a9f61
f97c5e8d018207b1d546501fe2036adfbf774cfd
Compromised servers used for command and control:
hxxps://cognimuse.cs.ntua.gr/search.php
hxxps://portal.sbn.co.th/rss.php
hxxps://97.75.120.45/news/archive.php
hxxps://portal.sbn.co.th/rss.php
hxxps://58.80.109.59/plugins/search.php
Compromised websites used to host CloudDuke:
hxxp://flockfilmseries.com/eFax/incoming/5442.ZIP
hxxp://www.recordsmanagementservices.com/eFax/incoming/150721/5442.ZIP
hxxp://files.counseling.org/eFax/incoming/150721/5442.ZIP
On 22/07/15 At 11:59 AM
Read More'Zero Days', The Documentary
VPRO (the Dutch public broadcasting organization) produced a 45-minute documentary about hacking and the trade of zero days. The documentary has now been released in English on YouTube.
The documentary features Charlie Miller, Joshua Corman, Katie Moussouris, Ronald Prins, Dan Tentler, Eric Rabe (of Hacking Team), Felix Lindner, Rodrigo Branco, Ben Nagy, The Grugq, and many others.
On 20/07/15 At 12:40 PM
Read MoreIOS Crash Report: Blocking "Pop-Ups" Doesn't Really Help
The Telegraph published an article on Thursday about a scam targeting iOS users. Here's the gist: scammers are using JavaScript generated dialogs to display warnings of so-called "IOS Crash" reports prompting people to call for tech support. Near the end of the Telegraph's article, the following advice is offered:
"To prevent the issue happening again, go to Settings -> Safari -> Block Pop-ups."
Unfortunately, this advice is incorrect. And perhaps even more unfortunately, some security and tech pundits are now repeating the bad advice on numerous websites. How do we know the advice is wrong? Because we actually tested it…
First of all, this "IOS Crash Report" scam is a variation of the technical support scam, cases of which have been documented as early as 2008. In the past, cold-calls originated directly from call centers in India. But more recently, web-based lures are used to prompt potential victims into contacting the scammers.
A Google Search returns several live scam sites with this text:
"Due to a third party application in your phone, IOS is crashed."
Here's one of the sites as viewed with iOS Safari on an iPad: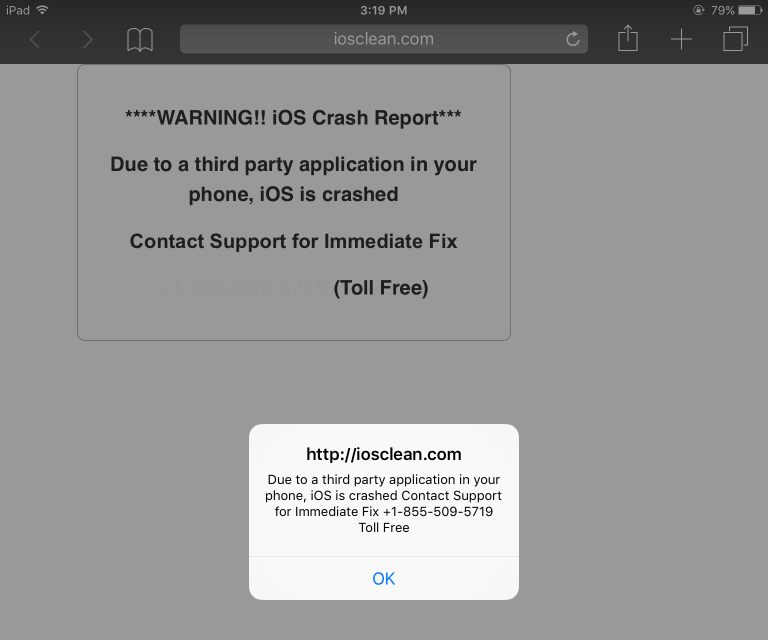
Safari's "Fraudulent Website Warning" and "Block Pop-ups" features didn't prevent the page from loading.
What looks like a pop-up on the image above is actually a JavaScript generated dialog. One which will continuously re-spawn itself and can be very difficult to dismiss. Turning off JavaScript in Safari is the quickest way to regain control. Unfortunately, leaving JavaScript disabled will significantly impact a large number of legitimate websites.
Here's the same site as viewed with Google Chrome for Windows: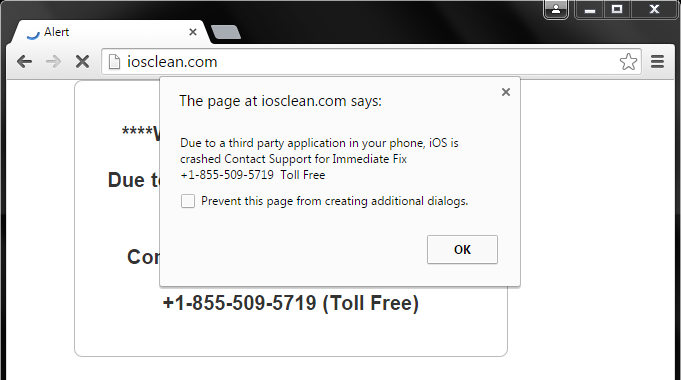
Notice the additional text in the image above: prevent this page from creating additional dialogs. Current versions of Chrome and Firefox (for Windows, at least) will inject this option into re-spawning dialogs, allowing the user to break the loop. Sadly, Internet Explorer and Safari do not. (We tested with IE for Windows / Windows Phone, and iOS Safari.)
Wouldn't be great if all browsers supported this prevention feature?
Yeah, we think so, too.
But it's not just browsers, apps with browser functionality can also be affected.
Here's an example of a JavaScript dialog displayed via Cydia.
The end of the Telegraph's article included the following advice from City of London police:
"Never give your iCloud username and password or your bank details to someone over the phone."
Indeed! Giving somebody your iCloud password could quickly turn a support scam into a data hijacking and extortion scheme. We attempted to call several of the scammer telephone numbers to see if they would ask for our iCloud credentials — only to discover that the numbers we tried are currently not in service.
Hopefully they stay that way. (They won't.)
On 17/07/15 At 10:15 AM
Read MoreHacking Team 0-day Flash Wave with Exploit Kits
After Hacking Team was compromised, a lot of information were publicly disclosed beginning 5th of July, particularly its business clients and a zero-day vulnerability for the Adobe Flash Player that they have been using.
Since the info about the first zero-day was made freely available, we knew attackers would swiftly move into using it. As expected, the flash exploit was integrated into exploit kits such as Angler, Magnitude, Nuclear, Neutrino, Rig, and HanJuan as reported by Kafeine.
Based on our telemetry, there was a rise in Flash exploits beginning 6th and continued until 9th.
Here are the stats for each exploit kit:
The security advisory for CVE-2015-5119 zero-day was released on 7th July and the patch was made available on 8th. So the hits started to decline about two days after the patch.
But just when people have started updating their systems, there was yet another spike from the Angler flash exploit hits:
Apparently, two more flash vulnerabilities, CVE-2015-5122 and CVE-2015-5123, were discovered. These vulnerabilities are still waiting to be patched. According to Kafeine, one of the two vulnerabilities were added into the Angler exploit kit.
As a side note related to Angler exploit kit, if you noticed in the second chart above, Angler and HanJuan share the same statistics. This was due to the fact that our detections for Angler Flash exploits were also hitting on HanJuan Flash exploits.
We have verified this after discovering that there was a different URL pattern being detected by Angler:
We looked at the flash exploit used by both kits, and the two are very much identical.
Angler Flash Exploit:
HanJuan Flash Exploit:
There were already speculations that there seem to be strong connections between the actors behind the two exploits kits. For example, both have used �fileless� delivery of payload and even similar encryption methods. Perhaps at some point we will see HanJuan supporting this new flash 0 day as well.
In the meantime, since there hasn�t been a patch out yet for these new ones, our users remain protected from the effects of the exploit kits through Browsing Protection as well as these detections:
Exploit:SWF/AnglerEK.L
Exploit:SWF/NeutrinoEK.C
Exploit:SWF/NeutrinoEK.D
Exploit:SWF/NuclearEK.H
Exploit:SWF/NuclearEK.J
Exploit:SWF/Salama.H
Exploit:SWF/Salama.R
Exploit:JS/AnglerEK.D
Exploit:JS/NuclearEK.I
Exploit:JS/MagnitudeEK.A
UPDATE: Adobe has released patches for the recent two vulnerabilities: CVE-2015-5122 and CVE-2015-5123. Users are recommended to update to the latest version of Adobe Flash Player.
On 13/07/15 At 12:29 PM
Read MoreThe Trusted Internet: Who governs who gets to buy spyware from surveillance software companies?
When hackers get hacked, that's when secrets are uncovered. On July 5th, Italian-based surveillance technology company Hacking Team was hacked. The hackers released a 400GB torrent file with internal documents, source code, and emails to the public - including the company's client list of close to 60 customers.
The list included countries such as Sudan, Kazakhstan and Saudi Arabia - despite official company denials of doing business with oppressive regimes. The leaked documents strongly implied that in the South-East Asian region, government agencies from Singapore, Thailand and Malaysia had purchased their most advanced spyware, referred to as a Remote Control System (RCS).
According to security researchers Citizen Lab, this spyware is extraordinarily intrusive, with the ability to turn on microphone and cameras on mobile devices, intercept Skype and instant messages, and use an anonymizer network of proxy servers to prevent harvested information from being traced back to the command and control servers.
Based on images of the client list posted to pastebin the software was purchased in Malaysia by the Malaysia Anti-Corruption Commission (MACC), Malaysia Intelligence (MI) and the Prime Minister's Office (PMO):
Additional images of leaked invoices posted to medium.com indicated the spyware was sold through a locally-based Malaysian company named Miliserv Technologies (M) Sdb Bhd (registered with the Ministry of Finance Malaysia), which specializes in providing digital forensics, intelligent gathering and public security services:

Why the Prime Minister's Office would need surveillance software remains puzzling. Mind you, professional grade spyware ain't cheap - a license upgrade could cost you MYR400, 000 and maintenance renewal will set you back about MYR160,000.
According to reports of the incident in Malaysian alternative media, Malaysian government agencies have probably been using the spyware even before discovery of the FinFisher malware that was detected in the run-up to the 2013 General Elections.
Coincidentally, Malaysia has also been the frequent host of the annual ISS World Asia tradeshow, where companies promote their arsenal of 'lawful' surveillance software to law enforcement agencies, telco service provider or government employees. During the 2014 event, the Hacking Team was present and the associate lead sponsor of the event.
MiliServ Technologies is currently involved in the upcoming 2015 ISS World Asia in Kuala Lumpur. The event is invitation-only � though it may be interesting to see if Hacking Team will make it there this year.
Post by – Su Gim
On 08/07/15 At 02:31 AM
Read MoreProblematic Wassenaar Definitions
The Wassenaar Arrangement, a multilateral export control regime, defines "intrusion software" as software specially designed or modified to avoid detection by monitoring tools, or to defeat protective countermeasures, of a computer or network capable device. Intrusion software is used to: extract data or information, or to modify system or user data; or to modify the standard execution path of a program or process in order to allow the execution of externally provided instructions.
Wassenaar states that monitoring tools are software or hardware devices that monitor system behaviours or processes running on a device. This includes antivirus (AV) products, end point security products, Personal Security Products (PSP), Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS) or firewalls.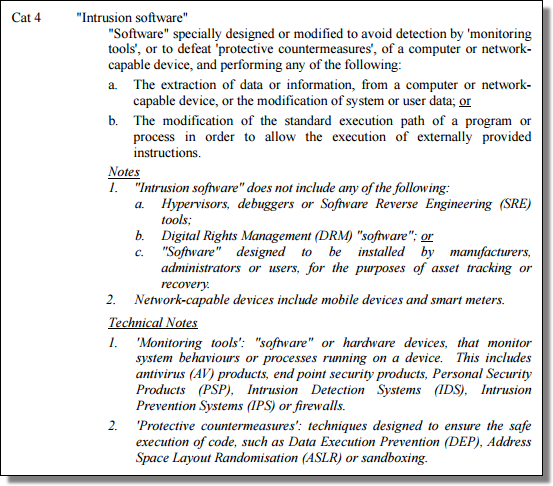
(Source)
So… what we at F-Secure (and the rest of the antivirus industry) call "malware" appears to easily fit Wassenaar's definition of intrusion software.
Why is this interesting?
Well, the US Bureau of Industry and Security (BIS), part of the US Department of Commerce, has proposed updating its rules to require a license for the export of intrusion software.
And according to the Dept of Commerce, "an export" is –any– item that is sent from the United States to a foreign destination. "Items" include among other things, software and technology.
The Paradox
So… if malware is intrusion software, and any item is an export, how exactly are US-based customers supposed to submit a malware sample to their European antivirus vendor? Seriously, customers send us zero-day using malware all the time. Not to mention the samples that we routinely exchange with other trusted AV vendors from around the globe.
Unintended Consequences
The text associated with the BIS proposal says the scope includes penetration testing products that use intrusion software in what looks like an attempt to limit "hacking" tools, but there is nothing about what is excluded from the scope. So the BIS might not intend to limit customers from uploading malware samples to their AV vendor, but that could be the effect if this new rule is adopted and arbitrarily enforced. Or else it could just force people to operate in a legal limbo. Is that what we want?
The BIS is taking comments until July 20th.
On 09/06/15 At 01:25 PM
Read MoreFound Item: UK Wi-Fi Law?
I visited the UK last Thursday, found a coffee shop offering "free" Wi-Fi, and read this…
"UK Law states that we must know who is using our Wi-Fi at all times."
Now I'm not a lawyer — but that seems like quite the disingenuous claim.
Mobile number, post code, and date of birth??
I wonder how many people fall for this type of malarkey.
Post by — @Sean
On 08/06/15 At 01:27 PM
Read MoreSMS Exploit Messages
There's an iOS vulnerability affecting iPhone, iPad, and even Apple Watch that allows for a denial of service.
Crashing a phone with an SMS? That's so 2008.
S60 SMS Exploit Messages
Unlike 2008, this time kids are reportedly using the vulnerability to harass others.
Apple is working on a security update. But unfortunately… that update very likely won't be available for older iPhones.
Updated to add:
Here's the "Effective Power" exploit crashing an iPhone 6:
Effective Power Unicode iOS hack on iPhone 6
And this… is Effective Power crashing the iOS Twitter app:
Effective Power Unicode iOS hack vs Twitter
On 28/05/15 At 01:56 PM
Read MoreRansomware Spam E-Mails Targeting Users in Italy and Spain
In the past few days, we received some cases from our customers in Italy and Spain, regarding malicious spam e-mails that pointed to Cryptowall or Cryptolocker ransomware.
The spam e-mails pretended to come from a courier/postal service, regarding a parcel that was waiting to be collected. The e-mails offer a link to track that parcel online:
When we did the initial investigation of the e-mails from our standard test system, the link redirected to Google: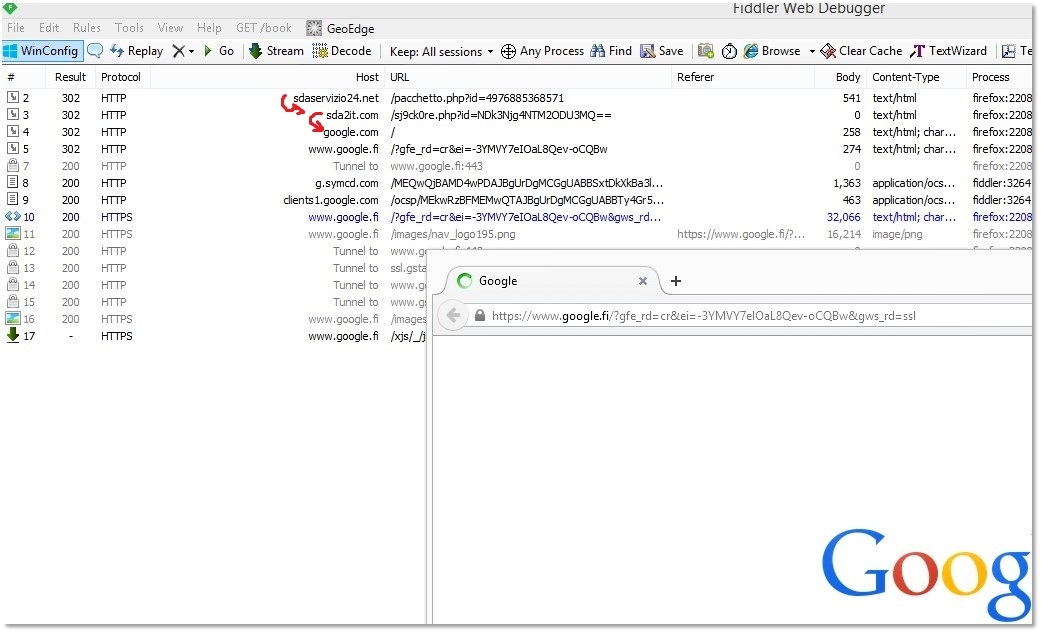
So, no malicious behavior? Well, we noted that the first two URLs were PHP. Since PHP code is executed on the server side, not locally on the client, it is possible that the servers were 'deciding' whether to redirect the user to Google or to serve malicious content, based on some preset conditions.
Since this particular spam e-mail is written in Italian - perhaps only a customer based in Italy would be able to see the malicious payload? Fortunately, we have Freedome, so we can travel to Italy for a little while to experiment.
So we turned on Freedome, set the location to Milan and clicked the link in the e-mail again: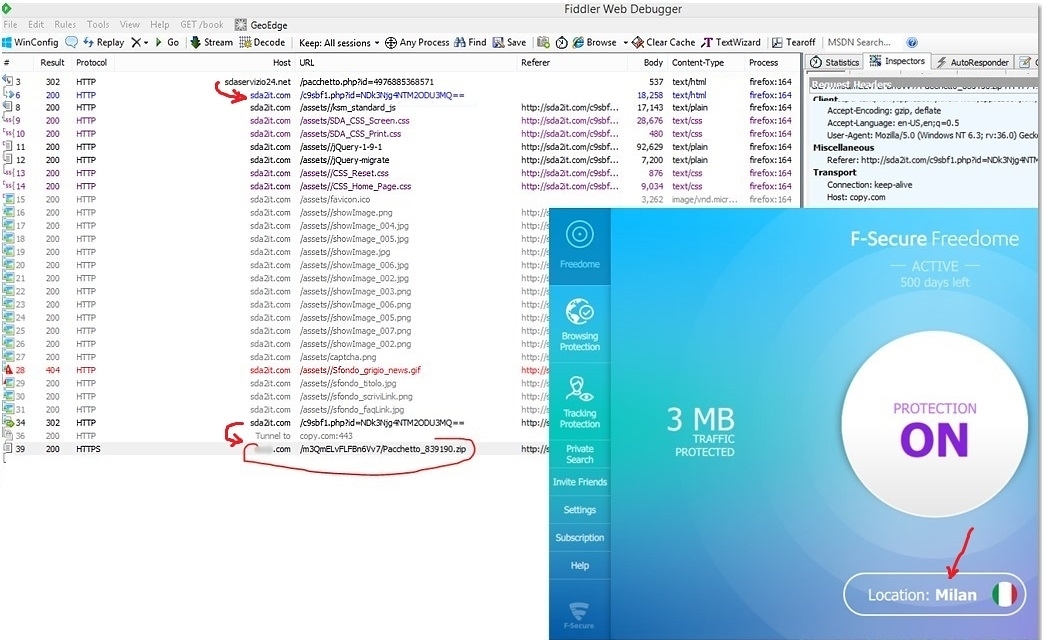
Now we see the bad stuff. If the user is (or appears to be) located in Italy, the server will redirect them to a malicious file hosted on a cloud storage server.
The e-mail spam sent to Spanish users is similar, though in those cases, a CAPTCHA challenge is included to make the site seem more authentic. If the link in the e-mail is clicked by a user located outside Spain, again we end up in Google:
If the site is visited instead from an Spanish IP, we get to the CAPTCHA screen:
And then to the malware itself:
This spam campaign doesn't use any exploits (so far), just old-fashioned social engineering; infection only occurs if the user manually downloads and executes the files offered on the malicious URLs. For our customers, the URLs are blocked and the files are detected.
(malware SHA1s: 483be8273333c83d904bfa30165ef396fde99bf2, 295042c167b278733b10b8f7ba1cb939bff3cb38)
Post by — Victor
On 19/05/15 At 03:17 AM
Read MoreMac Hack Demonstration
Securing your SSH password is very important. Otherwise, you might be pwned by a little girl with her Raspberry Pi.
Don't worry, it's an authorized hack, she asked her mom for permission.
On 15/05/15 At 12:46 PM
Read MoreEmail Security Considerations for Microsoft 365 Users
The post Email Security Considerations for Microsoft 365 Users appeared first on GreatHorn.
Read MoreEmail Security Considerations for Google Workspace Users
The post Email Security Considerations for Google Workspace Users appeared first on GreatHorn.
Read MoreShow the Value of Your Email Security Solutions: Don’t Just Measure Detection Rates
The post Show the Value of Your Email Security Solutions: Don’t Just Measure Detection Rates appeared first on GreatHorn.
Read MoreUniversities and Colleges Face Multi-faceted Email Security Challenges
The post Universities and Colleges Face Multi-faceted Email Security Challenges appeared first on GreatHorn.
Read MoreSpam vs Phish: The Problem with User-Reported Phish Buttons
The post Spam vs Phish: The Problem with User-Reported Phish Buttons appeared first on GreatHorn.
Read MorePhishing for Google Impersonation Attacks
Bad actors around the globe go phishing in emails twenty-four hours a day, seven days a week. Whether they are “guppies” like your local bakery down the street or big “fish” like Google, no one is immune to their attacks. Google, one of the largest, most well-known – and used – applications, will always be […]
The post Phishing for Google Impersonation Attacks appeared first on GreatHorn.
Read MoreGMX.Net Phishing Campaigns: Why They’re Hitting Users’ Inboxes
The post GMX.Net Phishing Campaigns: Why They’re Hitting Users’ Inboxes appeared first on GreatHorn.
Read MoreNative vs SEG vs ICES: What You Need to Know About Email Security
The shift from on-premise email platforms to cloud email platforms has taken shape, with the majority (70%) of organizations. Microsoft 365 and Google Workspace remain the predominant email platforms for organizations. However, a significant change has occurred in the past year. With an estimated 40% of ransomware attacks that start through email, and BEC and […]
The post Native vs SEG vs ICES: What You Need to Know About Email Security appeared first on GreatHorn.
Read MoreBlueberry Muffins vs Blonde Chihuahuas: Debunking Artificial Intelligence in Email Security
In cybersecurity, buzzwords come and go, often being replaced with new buzzwords while the market is still attempting to realize the benefits of the former. Today, every technology vendor is talking about Artificial Intelligence (AI). In reality, Machine Learning (the method to one day achieve AI) is still the predominant technical solution deployed within vendor […]
The post Blueberry Muffins vs Blonde Chihuahuas: Debunking Artificial Intelligence in Email Security appeared first on GreatHorn.
Read MoreGlobal Supply Chain: Attackers Targeting Business Deliveries
Our global supply chain includes all the people, companies and countries that need to work cohesively to manufacture, process and ship goods. Disruptions in the global supply chain are increasingly impacting organizations, with logistical problems crossing most industries. As a result, the continued strain on the supply chain puts added pressure on businesses as they […]
The post Global Supply Chain: Attackers Targeting Business Deliveries appeared first on GreatHorn.
Read MoreHeimdal 5.1.0 RC Dashboard: Smarter Automation, Stronger Compliance, and Smoother Control
The Heimdal 5.1.0 RC (Release Candidate) dashboard update is now live, bringing a powerful lineup of improvements designed to make IT management faster, safer, and more intuitive. From pre-built scripting and compliance dashboards to simpler agent management and refined privilege controls, this release takes another major step toward a fully unified cybersecurity experience. Smarter Automation […]
The post Heimdal 5.1.0 RC Dashboard: Smarter Automation, Stronger Compliance, and Smoother Control appeared first on Heimdal Security Blog.
Read MoreCan Generative AI Be Weaponized for Cyberattacks?
Generative AI has emerged as one of the most powerful technologies of our era. Capable of producing realistic text, images, voice, and even code, these systems are revolutionizing industries. But while they fuel innovation and productivity, they also introduce an entirely new class of threats. As AI capabilities grow, so too does the potential for […]
The post Can Generative AI Be Weaponized for Cyberattacks? appeared first on Heimdal Security Blog.
Read MoreDigital Warfare and the New Geopolitical Frontline
This article follows our recent article on the source of cybercrime attacks – read it here – we’re now exploring the global, commercial, and political dimensions of digital warfare. Key takeaways $100 billion in global cyber damages annually – equivalent to the GDP of a mid-sized nation. $400 million in business impact from a single […]
The post Digital Warfare and the New Geopolitical Frontline appeared first on Heimdal Security Blog.
Read MoreNearly 40% of 2024 Ransomware Payouts May Have Gone to Russia, China & North Korea
Ransomware victims paid an estimated $813 million in 2024. Nearly 40 percent of that may have gone to actors in Russia, China and North Korea, according to new analysis from cybersecurity firm Heimdal. Heimdal used recent telemetry, infrastructure tracing and ownership mapping to assess how ransomware revenue is likely distributed. The $813 million figure comes […]
The post Nearly 40% of 2024 Ransomware Payouts May Have Gone to Russia, China & North Korea appeared first on Heimdal Security Blog.
Read MoreWhat is Managed ITDR? Key Definitions, Features, and Benefits
Key takeaways: MITDR explained: Managed ITDR combines identity threat detection with expert-led response. Why it matters: Get better protection and lower costs without building a full in-house team. What to look for: Prioritize behavioral monitoring, real-time response, and expert oversight You’ve got the ITDR solution. That’s a good step towards effective account and identity-based threat […]
The post What is Managed ITDR? Key Definitions, Features, and Benefits appeared first on Heimdal Security Blog.
Read MoreRetail cybersecurity statistics for 2025
Cyber attacks against retail businesses have made headlines in 2025. Read this retail cybersecurity statistics rundown to understand more. For cyber criminals, the retail sector makes for a very attractive target. Retail businesses hold vast troves of valuable customer details, payment information and inventory data. What is more, any disruption caused by cyber crime is […]
The post Retail cybersecurity statistics for 2025 appeared first on Heimdal Security Blog.
Read MoreCyber Insurance Statistics for 2025
More and more businesses are taking out cyber insurance in 2025. Read our statistics rundown to understand why. Investing in cyber insurance is a smart move. In case of a cyber attack, it can reduce the financial burden of a breach and give businesses (and individuals) peace of mind. Advanced cybersecurity software should always be […]
The post Cyber Insurance Statistics for 2025 appeared first on Heimdal Security Blog.
Read MoreIs Your Tech Stack Killing Profitability? The Silent Bug Crippling MSP Growth
Many MSPs want to grow, but internal complexity often holds them back. In this guest article, Portland, a Heimdal partner, breaks down how fragmented systems and unclear value messaging can quietly erode profits, compliance, and trust – and how to fix it. The “system bug” holding MSPs back “Stop talking about technology. Start talking about […]
The post Is Your Tech Stack Killing Profitability? The Silent Bug Crippling MSP Growth appeared first on Heimdal Security Blog.
Read MoreCybersecurity Has a Motivation Problem
I’ve worked in cybersecurity long enough to see that our biggest challenge isn’t a technical one, it’s motivational. We can build the strongest firewalls, design the smartest detection systems, and run endless awareness campaigns, but none of it matters if people don’t want to care. That’s the uncomfortable truth; cyber security has a motivation problem. […]
The post Cybersecurity Has a Motivation Problem appeared first on Heimdal Security Blog.
Read MoreAgent Fatigue Is Real and Your Security Stack Is to Blame
Your senior analyst stares at alert number 47. It’s not even lunch. Another “suspicious login detected.” They switch to the third dashboard of the morning, cross-reference the user activity, and confirm what they already knew. Bob from accounting is working late again. Meanwhile, three dashboards over, actual lateral movement is happening on a client’s network. […]
The post Agent Fatigue Is Real and Your Security Stack Is to Blame appeared first on Heimdal Security Blog.
Read MoreHeimdal 5.0.0 RC: RDP Protection, Ransomware Detection, and OS Deployment
Version 5.0.0 adds three major features for MSPs. a module that controls RDP access an improved ransomware detection engine a simpler way to deploy Windows over the network. Remote Access Protection (RAP): Block Unauthorized RDP Attempts RDP brute-force attacks remain a top breach vector, so we built a new module that monitors and filters Remote […]
The post Heimdal 5.0.0 RC: RDP Protection, Ransomware Detection, and OS Deployment appeared first on Heimdal Security Blog.
Read MoreWhere Ransomware Profits Go and How to Cut Them Off
Researched and written by Heimdal founder Morten Kjaersgaard, this article exposes how even limited cooperation between registry bodies and law enforcement could cripple ransomware networks and raise the cost for cybercriminals. This article serves as a wake-up call. Even limited cooperation between registry bodies and law enforcement could cripple ransomware networks and raise the cost […]
The post Where Ransomware Profits Go and How to Cut Them Off appeared first on Heimdal Security Blog.
Read MoreITDR vs EDR: What are the Key Differences?
Key takeaways: What are the main differences between ITDR, EDR, and other security solutions? How does ITDR provide effective protection against identity-based threats? How to effectively detect and respond to attacks. If there’s one thing the cybersecurity community loves, it’s an acronym. To some extent, this has been the case since the earliest days of cybersecurity. […]
The post ITDR vs EDR: What are the Key Differences? appeared first on Heimdal Security Blog.
Read MoreWhat Is Identity Threat Detection and Response?
Key insights: What is identity threat detection and response (ITDR)? What are the differences and similarities between ITDR and EDR? What are the alternatives to ITDR? Identity Threat Detection and Response (ITDR) is a comparatively new term in the cybersecurity scene. It was first coined by Gartner in 2022 and has since become a cornerstone […]
The post What Is Identity Threat Detection and Response? appeared first on Heimdal Security Blog.
Read MoreSmall Business Cybersecurity Statistics in 2025
Small businesses are a big target for cyber criminals. Read our small business statistics rundown to get a true picture of how the sector is being affected in 2025. Until relatively recently, cybercrime wasn’t perceived as a major risk for small businesses. Hackers traditionally focused on larger companies or government bodies with more money and […]
The post Small Business Cybersecurity Statistics in 2025 appeared first on Heimdal Security Blog.
Read MoreYARA-X 1.10.0 Release: Fix Warnings, (Sun, Nov 23rd)
YARA-X&#;x26;#;39;s 1.10.0 release brings a new command: fix warnings.
Read MoreWireshark 4.4.1 Released, (Sun, Nov 23rd)
Wireshark release 4.6.1 fixes 2 vulnerabilities and 20 bugs.
Read MoreUse of CSS stuffing as an obfuscation technique?, (Fri, Nov 21st)
From time to time, it can be instructive to look at generic phishing messages that are delivered to one's inbox or that are caught by basic spam filters. Although one usually doesn't find much of interest, sometimes these little excursions into what should be a run-of-the-mill collection of basic, commonly used phishing techniques can lead one to find something new and unusual. This was the case with one of the messages delivered to our handler inbox yesterday…
Read MoreISC Stormcast For Friday, November 21st, 2025 https://isc.sans.edu/podcastdetail/9710, (Fri, Nov 21st)
No summary available.
Read MoreOracle Identity Manager Exploit Observation from September (CVE-2025-61757), (Thu, Nov 20th)
Searchlight Cyber today released a blog detailing CVE-2025-61757, a vulnerability they reported to Oracle. Oracle released a patch for the vulnerability as part of its October Critical Patch Update, which was released on October 21st.
Read MoreISC Stormcast For Thursday, November 20th, 2025 https://isc.sans.edu/podcastdetail/9708, (Thu, Nov 20th)
No summary available.
Read MoreUnicode: It is more than funny domain names., (Wed, Nov 12th)
When people discuss the security implications of Unicode, International Domain Names (IDNs) are often highlighted as a risk. However, while visible and often talked about, IDNs are probably not what you should really worry about when it comes to Unicode. There are several issues that impact application security beyond confusing domain names.
Read MoreISC Stormcast For Wednesday, November 19th, 2025 https://isc.sans.edu/podcastdetail/9706, (Wed, Nov 19th)
No summary available.
Read MoreISC Stormcast For Tuesday, November 18th, 2025 https://isc.sans.edu/podcastdetail/9704, (Tue, Nov 18th)
No summary available.
Read MoreReport: Deepfake Attacks Are on the Rise
A new report from Entrust warns of an increase in deepfake attacks, which now account for one in five biometric fraud attempts. Additionally, instances of deepfaked selfies have increased by 58% over the past year.
Read MoreReport: Ransomware Attacks Surged Globally in October
Ransomware attacks spiked in October 2025, with more than 700 organizations sustaining attacks, according to a new report from Cyfirma.
Read MoreHow KnowBe4 Uses AI Efficiently to Get the Best Results
Using the right tool for the job is always better.
Anyone who does DIY projects around the home knows how using the right tool can dramatically make the job you are doing far easier. Use the wrong tool, and that task suddenly becomes a burdensome nightmare.
Read MoreWarning: New Phishing Kit Targets Italian Entities
A new phishing kit is impersonating the Italian IT and web services provider Aruba, according to researchers at Group-IB. The kit is designed to trick users into entering their Aruba credentials, granting attackers access to sensitive accounts.
Read MoreNew Android Malware Platform Targets Bank Accounts
Researchers at Zimperium are tracking a new malware-as-a-service platform designed to target Android phones with banking Trojans. The platform, dubbed “Fantasy Hub,” allows unskilled threat actors to launch sophisticated malware campaigns that trick victims into granting access to their bank accounts.
Read More2025 Cybersecurity Awareness Month by the Numbers
Organizations rely on KnowBe4 to educate millions of people each month on security awareness and compliance topics, and every October, during Cybersecurity Awareness Month, engagement with our training content sets new records. 2025 was no exception.
Read MoreYour KnowBe4 Compliance Plus Fresh Content Updates from October 2025
We’re thrilled to announce KnowBe4 Studios, uniting our world-class creative teams under one powerful brand for our Compliance Plus library. Leveraging the latest AI technologies and the expertise of our global content creators, we’re set to produce more engaging compliance training than ever before—including fresh microcontent, interactive games and expanded storytelling experiences. This evolution marks the next phase in our quest to disrupt compliance training, which in combination with our security awareness training, helps your organization rise above risk.
Read MoreTycoon 2FA Phishing Kit Grows More Sophisticated
Cybereason warns that the Tycoon 2FA phishing kit continues to receive upgrades, allowing unskilled cybercriminals to launch sophisticated social engineering attacks. The platform is known for its ability to bypass multi-factor authentication measures.
Read MoreMY TAKE: Carol Sturka declares ‘I have agency!’ — Big Tech’s AI models now testing that claim
It was a tense moment in Episode 4 of Pluribus, the Apple TV series about a world linked by a single intelligence.
Related: Mistaking pattern mastery for wisdom
A character named Carol Sturka, surrounded by a seemingly benevolent collective … (more…)
The post MY TAKE: Carol Sturka declares ‘I have agency!’ — Big Tech’s AI models now testing that claim first appeared on The Last Watchdog.
Read MoreNews alert: Seraphic evolves browser security for the AI era with first-of-its-kind Electron protection
TEL AVIV, Nov. 19, 2025, CyberNewswire — Seraphic, the leader in enterprise browser security (SEB) and AI enablement, today announced native protection for Electron-based applications such as ChatGPT desktop, Teams, Slack, and more, becoming the first and only browser … (more…)
The post News alert: Seraphic evolves browser security for the AI era with first-of-its-kind Electron protection first appeared on The Last Watchdog.
Read MoreNews alert: ‘Shopping Cart Inspect’ wins top award for stopping online payment skimming in real time
OREM, Utah, Nov. 18, 2025, CyberNewswire — Security Metrics, a leading innovator in compliance and cybersecurity, today announced that its Shopping Cart Inspect (SCI) solutions has been selected as winner of the “Data Leak Detection Solution of the Year” … (more…)
The post News alert: ‘Shopping Cart Inspect’ wins top award for stopping online payment skimming in real time first appeared on The Last Watchdog.
Read MoreNews alert: SquareX exposes obscure AI browser flaw that gives extensions full access to user devices
PALO ALTO, Calif., Nov. 19, 2025, CyberNewswire — SquareX released critical research exposing a hidden API in Comet that allows extensions in the AI Browser to execute local commands and gain full control over users’ devices.
 The research reveals that … (more…)
The research reveals that … (more…)
The post News alert: SquareX exposes obscure AI browser flaw that gives extensions full access to user devices first appeared on The Last Watchdog.
Read MoreNews alert: CredShields and Checkmarx partner to extend AppSec into Web3 and smart contracts
SINGAPORE, Nov. 19, 2025, CyberNewswire — The collaboration advances enterprise grade application security into decentralized ecosystems, uniting Checkmarx’s AppSec expertise with Web3 specialization by CredShields.
 CredShields, a leading Web3 security firm, has partnered with Checkmarx, the global leader … (more…)
CredShields, a leading Web3 security firm, has partnered with Checkmarx, the global leader … (more…)
The post News alert: CredShields and Checkmarx partner to extend AppSec into Web3 and smart contracts first appeared on The Last Watchdog.
Read MoreNews alert: Secure.com debuts AI-native ‘Digital Security Teammate’ to help lean security teams
LOS ANGELES and DUBAI, United Arab Emirates, Nov. 18, 2025 – Secure.com today announced the launch of Digital Security Teammate (DST), a new category of AI-native agents built to help security teams survive the largest operational crisis the industry has … (more…)
The post News alert: Secure.com debuts AI-native ‘Digital Security Teammate’ to help lean security teams first appeared on The Last Watchdog.
Read MoreFIRESIDE CHAT: Edge AI moves onto the silicon layer, redefining how connected systems run
One of the more surprising — and least visible — frontiers of artificial intelligence today is unfolding at the extreme edges of our hyper-connected systems.
Related: AI adoption outpacing controls
Think sensors in forests that detect illegal logging. Smart speakers … (more…)
The post FIRESIDE CHAT: Edge AI moves onto the silicon layer, redefining how connected systems run first appeared on The Last Watchdog.
Read MoreNews alert: SpyCloud forecasts Top 10 identity threats set to define 2026 security landscape
AUSTIN, Texas, Nov. 18, 2025, CyberNewswire — SpyCloud, the leader in identity threat protection, today released its report, The Identity Security Reckoning: 2025 Lessons, 2026 Predictions, outlining 10 of the top trends that will shape the cyber threat … (more…)
The post News alert: SpyCloud forecasts Top 10 identity threats set to define 2026 security landscape first appeared on The Last Watchdog.
Read MoreShared Intel Q&A: Viewing CMMC as a blueprint for readiness across the defense supply chain
Small and mid-sized contractors play a vital role in the U.S. defense industrial base — but too often, they remain the weakest link in the cybersecurity chain.
Related: Pentagon enforcing CMMC
RADICL’s 2025 DIB Cybersecurity Maturity Report reveals that 85% … (more…)
The post Shared Intel Q&A: Viewing CMMC as a blueprint for readiness across the defense supply chain first appeared on The Last Watchdog.
Read MoreMY TAKE: AI’s fortune-teller effect — why it’s all too easy to mistake pattern mastery for wisdom
I hadn’t expected the machine’s answer to be that good.
Related: The AI bubble is inflating
It was a simple prompt — I needed help crafting a reply to a client. One of those mid-project check-ins where timing gets murky … (more…)
The post MY TAKE: AI’s fortune-teller effect — why it’s all too easy to mistake pattern mastery for wisdom first appeared on The Last Watchdog.
Read MoreAI teddy bear for kids responds with sexual content and advice about weapons
FoloToy's AI teddy bear, Kumma, crossed serious lines, raising fresh concerns about how little oversight exists for AI toys marketed to children.
Read MoreFake calendar invites are spreading. Here’s how to remove them and prevent more
Calendar spam is a growing problem, often arriving as email attachments or as download links in messaging apps.
Read MoreBudget Samsung phones shipped with unremovable spyware, say researchers
Samsung is under fire again for shipping phones in parts of the world with a hidden system app, AppCloud, that users can’t easily remove.
Read MoreWhat the Flock is happening with license plate readers?
What Flock's ALPR cameras really collect, how they’re used in neighborhoods, and what you can do to stay in control.
Read MoreHoliday scams 2025: These common shopping habits make you the easiest target
Holiday deals are flooding your phone, and scammers are too. Watch for fake listings, phishing texts, and offers that seem just a little too good to be true.
Read More[Correction] Gmail can read your emails and attachments to power “smart features”
Did you know that Gmail can use your emails and attachments for its smart features? Here's how to check your settings.
Read MoreMac users warned about new DigitStealer information stealer
DigitStealer is a new infostealer built for macOS, and it stands out for being smarter than most. Here's how it works and how to stay safe.
Read MoreAttackers are using “Sneaky 2FA” to create fake sign-in windows that look real
The Phishing-as-a-Service kit Sneaky 2FA was found to use Browser-in-the-Browser attacks to steal login credentials.
Read MoreSharenting: are you leaving your kids’ digital footprints for scammers to find?
Our children build digital lives long before they understand them. Here’s how to shrink their online footprint and stay smart about “sharenting.”
Read MoreChrome zero-day under active attack: visiting the wrong site could hijack your browser
Google has released an update to patch two high-severity vulnerabilities, one of which is already under active exploitation.
Read MoreThieves order a tasty takeout of names and addresses from DoorDash
It was the way DoorDash handled the communication of the breach, as much as the data leaked, that has angered customers.
Read MoreWhy it matters when your online order is drop-shipped
Those too-good-to-be-true online deals often come from drop-shipping sellers, and that can leave you holding all the risk.
Read MoreThe price of ChatGPT’s erotic chat? $20/month and your identity
This is how surveillance gets normalized: one “safety” feature at a time.
Read MoreYour coworker is tired of AI “workslop” (Lock and Code S06E23)
This week on the Lock and Code podcast, we speak with Dr. Kristina Rapuano about AI "workslop" and its impact on people and their attitudes.
Read MoreScammers are sending bogus copyright warnings to steal your X login
A copyright violation sounds serious, so cybercriminals are faking messages from the DMCA to lure you into handing over your X credentials.
Read MoreA week in security (November 10 – November 16)
A list of topics we covered in the week of November 10 to November 16 of 2025
Read MoreBe careful responding to unexpected job interviews
Contacted out of the blue for a virtual interview? Be cautious. Attackers are using fake interviews to slip malware onto your device.
Read MoreYour passport, now on your iPhone. Helpful or risky?
Apple's Digital ID makes travel smoother and saves you from digging for documents, but it comes with privacy and security trade-offs. We break down the pros and cons.
Read More1 million victims, 17,500 fake sites: Google takes on toll-fee scammers
Google’s suing Lighthouse, a Chinese Phishing-as-a-Service platform that uses Google’s branding on scam sites to trick victims.
Read MoreAre you paying more than other people? NY cracks down on surveillance pricing
New York is calling out data-driven pricing, where algorithms use your clicks, location and search history to tweak what you pay.
Read MoreWhat AWS and Cloudflare Outages Teach Us About Cloud Configuration Risks
On Tuesday, 18 November, a Cloudflare outage took a significant part of the Internet offline, including major sites, enterprise platforms and public-facing services. Ironically, even Downdetector – the platform that provides real-time information about service outages – apparently went down for a time. This wasn’t an isolated incident, either: an AWS (Amazon Web Services) outage about a month ago caused similar disruption to thousands of dependent services and was followed a few days later by a smaller Microsoft Azure outage. If the largest Cloud providers can experience outages of this size, it’s no great stretch to suggest that all organisations
The post What AWS and Cloudflare Outages Teach Us About Cloud Configuration Risks appeared first on IT Governance Blog.
Read MorePhishing Season 2025: How AI is Supercharging Cyber Crime
Phishing attacks tend to peak at the end of each year as criminals exploit seasonal pressure and distracted staff to increase the intensity of their campaigns. In 2025, the threat is increasing once again – only this time, AI-generated phishing has moved from a niche tactic to an everyday tool for cyber criminals. This article explains why “phishing season” matters, the trends expected this year and the steps organisations can take to harden their defences. Why phishing peaks at this time of year Phishing activity always rises sharply in Q4. The pattern is consistent across recent breach surveys and confirmed
The post Phishing Season 2025: How AI is Supercharging Cyber Crime appeared first on IT Governance Blog.
Read MoreThe Data (Use and Access) Act and How it Affects the UK GDPR and DPA 2018, and PECR
Enacted in June, the Data (Use and Access) Bill – now the Data (Use and Access) Act 2025 or ‘DUAA’ – marked a significant moment in the evolution of UK data protection legislation. The Act builds on previous legislative efforts – most notably 2022’s shelved DPDI (Data Protection and Digital Information) Bill – and brings together key reforms under one cohesive framework. While its principal focus is to reform the UK GDPR (General Data Protection Regulation and DPA (Data Protection Act) 2018, and the PECR (Privacy and Electronic Communications Regulations), the DUAA is far more than a privacy update. It
The post The Data (Use and Access) Act and How it Affects the UK GDPR and DPA 2018, and PECR appeared first on IT Governance Blog.
Read MoreGlobal Data Breaches and Cyber Attacks in October 2025 – At Least 21.2 Million Breached Records
Summary Welcome to another monthly round-up of monthly cyber attack and data breach news. October 2025 saw 20 publicly reported cyber attacks and data breaches around the globe. In total, at least 21.2 million records were confirmed to have breached As ever, these are the incidents that made the news this month – the list is, by necessity, far from exhaustive. The month’s five largest incidents Prosper Marketplace Dukaan Allianz Life Insurance Company of North America WestJet Motility Software Solutions Trends in October 2025 Key vulnerabilities exploited List of data breaches and cyber attacks disclosed in October 2025 Disclosure date Organisation
The post Global Data Breaches and Cyber Attacks in October 2025 – At Least 21.2 Million Breached Records appeared first on IT Governance Blog.
Read MoreGRC Solutions Named Among the UK’s Top 20 Cyber Security Innovators
We’re delighted to announce that GRC Solutions – the new name for IT Governance – has been recognised as one of the UK’s leading cyber security companies, ranking 19th in TechRound’s Cybersecurity40 2025 list. The annual campaign celebrates the most innovative and forward-thinking cyber security organisations across the UK and Europe, highlighting those helping businesses and public bodies stay secure in an increasingly complex threat landscape. TechRound – the UK’s independent voice for startups and the wider technology sector – evaluates entrants based on innovation, impact and contribution to the cyber security industry. The 2025 list showcases a diverse range
The post GRC Solutions Named Among the UK’s Top 20 Cyber Security Innovators appeared first on IT Governance Blog.
Read MoreData Leakage Prevention and Data Deletion – ISO 27001 Controls 8.12 and 8.12 Explained
ISO 27001:2022 introduced several new controls designed to reflect modern security practices and the ways organisations use and manage data. Two of the most practical additions sit in the operational controls: 8.12 (data leakage prevention) and 8.10 (data deletion). Both address longstanding weaknesses in many ISMSs (information security management systems). They focus on the lifecycle of data, the risks created by its movement and the need to prevent unnecessary retention. They also bring ISO 27001 closer to regulatory expectations, particularly around access control, monitoring and data minimisation. This blog post explains what the two controls require, why they were introduced
The post Data Leakage Prevention and Data Deletion – ISO 27001 Controls 8.12 and 8.12 Explained appeared first on IT Governance Blog.
Read MoreThreat Intelligence – ISO 27001:2022 Control 5.7 Explained
Cyber attacks evolve faster than traditional security review cycles. So, to stay secure, organisations need a clearer understanding of the threats that are most relevant to their systems, data and business operations. Threat intelligence is the process of collecting and analysing information about these threats so that security decisions are informed by real-world attack patterns rather than theoretical risk models. Done well, it enables organisations to both pre-empt attacks and respond more effectively when incidents happen. This is the purpose of ISO 27001:2022 control 5.7. As one of 11 new controls introduced by the 2022 iteration of the Standard, it
The post Threat Intelligence – ISO 27001:2022 Control 5.7 Explained appeared first on IT Governance Blog.
Read MoreHow DORA fits with ISO 27001, NIS2 and the GDPR
Although DORA (the EU Digital Operational Resilience Act) has been in effect since January 2025, organisations that supply the EU’s financial services sector are under growing pressure to demonstrate compliance with its requirements. For most, this isn’t about starting from scratch but about mapping what’s already in place, identifying where DORA goes further and then expanding on current practices. After all, DORA builds on – not replaces – established frameworks, standards and other compliance regimes such as ISO 27001, NIS2 (the Network and Information Security Directive 2) and the GDPR (General Data Protection Regulation). It formalises ICT risk governance for
The post How DORA fits with ISO 27001, NIS2 and the GDPR appeared first on IT Governance Blog.
Read MoreCISM Exam Tips from a Consultant: Five Insider Insights to Help You Pass
The CISM® (Certified Information Security Manager) exam is one of the toughest in the field – according to most providers, pass rates are around 60–65% (ISACA doesn’t publish official figures). Even experienced professionals find it demanding, something our consultants know first-hand. Soji Ogunjobi is a cyber security specialist and instructor, with nearly two decades of experience as a cyber security professional and IT auditor. He also has an MSc in Information Technology, Computer and Information Systems, as well as CISM, CISSP, CISA, CCSP and various other cyber security qualifications. Below are five practical CISM exam tips drawn directly from his
The post CISM Exam Tips from a Consultant: Five Insider Insights to Help You Pass appeared first on IT Governance Blog.
Read MoreHow To Comply with ISO 27001’s New Cloud Services Control
The 2022 update to ISO 27001 introduced a new control for the use of Cloud services. It outlines the policies and procedures that are required when acquiring, using, managing or exiting Cloud services. Adding this control was an obvious and necessary step given just how many organisations use Cloud services as part of their core business activities. An estimated 96% of all organisations use at least one Internet-based IT resource, such as Amazon Web Services or Microsoft Azure. Whenever an organisation implements a new resource on which sensitive data is stored or upon which key business activities rely, it must
The post How To Comply with ISO 27001’s New Cloud Services Control appeared first on IT Governance Blog.
Read MoreToddyCat: your hidden email assistant. Part 1
Kaspersky experts analyze the ToddyCat APT attacks targeting corporate email. We examine the new version of TomBerBil, the TCSectorCopy and XstReader tools, and methods for stealing access tokens from Outlook.
Read MoreInside the dark web job market
This report examines how employment and recruitment function on the dark web, based on over 2,000 job-related posts collected from shadow forums between January 2023 and June 2025.
Read MoreBlockchain and Node.js abused by Tsundere: an emerging botnet
Kaspersky GReAT experts discovered a new campaign featuring the Tsundere botnet. Node.js-based bots abuse web3 smart contracts and are spread via MSI installers and PowerShell scripts.
Read MoreIT threat evolution in Q3 2025. Mobile statistics
The report features statistics on mobile threats for the third quarter of 2025, along with interesting findings and trends from the quarter, including an increase in ransomware activity in Germany, and more.
Read MoreIT threat evolution in Q3 2025. Non-mobile statistics
The report presents key trends and statistics on malware that targets personal computers running Windows and macOS, as well as Internet of Things (IoT) devices, during the third quarter of 2025.
Read MoreCrypto wasted: BlueNoroff’s ghost mirage of funding and jobs
Kaspersky GReAT experts dive deep into the BlueNoroff APT's GhostCall and GhostHire campaigns. Extensive research detailing multiple malware chains targeting macOS, including a stealer suite, fake Zoom and Microsoft Teams clients and ChatGPT-enhanced images.
Read MoreMem3nt0 mori – The Hacking Team is back!
Kaspersky researchers discovered previously unidentified commercial Dante spyware developed by Memento Labs (formerly Hacking Team) and linked it to the ForumTroll APT attacks.
Read MoreDeep analysis of the flaw in BetterBank reward logic
Kaspersky experts break down the recent BetterBank incident involving ESTEEM token bonus minting due to the lack of liquidity pool validation.
Read MoreThe evolving landscape of email phishing attacks: how threat actors are reusing and refining established techniques
Common email phishing tactics in 2025 include PDF attachments with QR codes, password-protected PDF documents, calendar phishing, and advanced websites that validate email addresses.
Read MorePassiveNeuron: a sophisticated campaign targeting servers of high-profile organizations
Kaspersky GReAT experts break down a recent PassiveNeuron campaign that targets servers worldwide with custom Neursite and NeuralExecutor APT implants and Cobalt Strike.
Read More
.png)
.png)
.png)














.png)
